 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide
 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
Cross-domain cryptographic sessions in which both hosts use ICSF/MVS z/OS Communications Server: SNA Network Implementation Guide SC27-3672-01 |
|
|
To allow cross-domain cryptographic sessions to be established, file SLU keys for each domain as described in Single-domain cryptographic sessions that use ICSF/MVS. Then use ICSF/MVS to file cross-domain keys on the cryptographic key data set (CKDS) at each host processor as described in the following paragraphs. A complementary pair of exporter and importer keys must be generated
for the two host processors (HOST1 and HOST2). To allow for cross-domain
cryptographic sessions between hosts using the ICSF/MVS cryptographic
service, perform the following steps:
Figure 1 illustrates the possible coding for cross-domain cryptographic sessions where both hosts use ICSF/MVS. APPL2A can initiate a cryptographic session with LU1A. APPL1A can initiate a cryptographic session with LU2A. APPL2A can be the PLU in a cryptographic session with APPL1A. However, APPL2A cannot be the SLU in a session with APPL1A because there is no TYPE(IMPORTER) statement coded in VTAM2, and APPL2A requires cryptography when it is the SLU. Figure 1. Cryptography in multiple-domain environment (Both
hosts use ICSF/MVS)
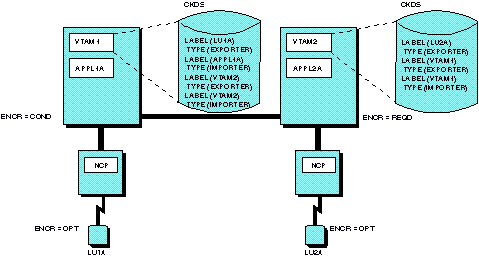 For the configuration in Figure 1 to have any encrypted sessions, start cryptography in both hosts before activating a session. For more information about ICSF/MVS, see the z/OS Cryptographic Services ICSF Administrator's Guide. 

|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |