 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide
 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
Cross-domain cryptographic sessions in which both hosts use PCF/CUSP z/OS Communications Server: SNA Network Implementation Guide SC27-3672-01 |
|
|
To allow cross-domain cryptographic sessions to be established,
file SLU keys for each domain as described in Single-domain cryptographic sessions that use PCF/CUSP. Start the PCF/CUSP compatible cryptographic product before
you activate the external CDRM for which cross statements have been
filed in the cryptographic keys data set. Use the PCF/CUSP compatible
cryptographic product to file cross-domain keys on the cryptographic
key data set (CKDS) at each host processor as follows:
Figure 1 illustrates the possible coding for cross-domain cryptographic sessions where both hosts use PCF/CUSP. APPL2A can initiate a cryptographic session with LU1A. APPL2A can be the primary LU (PLU) in the cryptographic session with APPL1A. However, APPL2A cannot be the secondary LU in a cryptographic session with APPL1A because there is no REMOTE statement for APPL2A in VTAM2. Figure 1. Cryptography in multiple-domain environment (Both
hosts use PCF/CUSP)
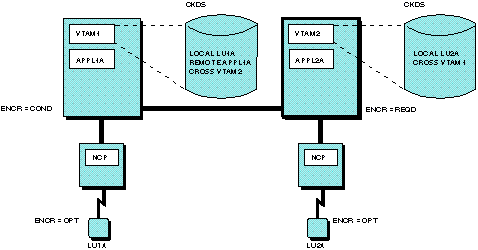 For the configuration in Figure 1 to have any encrypted sessions, start cryptography in both hosts before activating a session. 1 The terms local and remote in reference to the keys used by the CROSS statement do
not have the same meaning here as they do in other contexts in this
document. For more information about PCF, see the z/OS Cryptographic Services ICSF Application
Programmer's Guide. For more information about CUSP, see the z/OS Cryptographic Services ICSF Administrator's
Guide.


|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |