In this description of possible coding, assume that ICSF/MVS is
installed in HOST1 and a PCF/CUSP compatible cryptographic product
is installed in HOST2. A complementary pair of key-encrypting keys
must be generated for HOST1 and HOST2. To allow for cross-domain cryptographic
sessions between the hosts, perform one of the following, depending
upon where key processing is to be performed first:
-
When key processing is to be performed from HOST2 first, perform
these steps:
- At HOST2 where the PCF/CUSP compatible cryptographic product is
installed, code the following key generation utility program (KGUP)
statement:
CROSS name
Where name is the name of HOST1 CDRM.
This PCF/CUSP KGUP statement generates a LOCAL and REMOTE key
pair and places them in HOST2 cryptographic key data set (CKDS). A
copy of the key pair generated will also appear in the KGUP SYSPRINT
output listing. This gives HOST2 the capability to send encrypted
session keys to HOST1.
- At HOST1, use the PCF/CUSP compatible cryptographic product SYSPRINT
output from the cross key pair to create the following ICSF control
statement for the appropriate environment.
- When HOST2 has PCF
ADD LABEL(name) TYPE(IMPORTER) CLEAR NOCV KEY(key-value)
- When HOST2 has CUSP
ADD LABEL(name) TYPE(IMPORTER) CLEAR NOCV KEY(key-value,ikey)
where:
- name is the name of HOST2 CDRM.
- key-value is the key value from HOST2
of the local key.
- ikey is the intermediate key value
from HOST2 of the intermediate local key.
This ICSF KGUP statement places the importer key, which
is the same clear value as HOST2 LOCAL key in HOST1 CKDS. This allows
HOST1 to decrypt session keys sent from HOST2.
- At HOST1, use the PCF/CUSP compatible cryptographic product SYSPRINT
output from the cross-key pair to create the following ICSF control
statement for the appropriate environment.
- When HOST2 has PCF
ADD LABEL(name) TYPE(EXPORTER) CLEAR NOCV KEY(key-value)
- When HOST2 has CUSP
ADD LABEL(name) TYPE(EXPORTER) CLEAR NOCV KEY(key-value,ikey)
where:
- name is the name of HOST2 CDRM.
- key-value is the key value from HOST2
of the remote key.
- ikey is the intermediate key value
from HOST2 of the intermediate remote key.
This ICSF KGUP statement places the exporter key, which
has the same clear value as HOST2 REMOTE key, in HOST1 CKDS. This
allows HOST1 to send encrypted session keys to HOST2.
-
When key processing is to be performed from HOST1 first, perform
these steps:
- At HOST1 where ICSF/MVS is installed, code the appropriate key
generation utility program (KGUP) statements listed below for the
environment in HOST2:
- When HOST2 has PCF
ADD LABEL(name) TYPE(EXPORTER) CLEAR NOCV SINGLE
ADD LABEL(name) TYPE(IMPORTER) CLEAR NOCV SINGLE
- When HOST2 has CUSP
ADD LABEL(name) TYPE(EXPORTER) CLEAR NOCV
ADD LABEL(name) TYPE(IMPORTER) CLEAR NOCV
where name is the name
of HOST2 CDRM.
These statements cause two keys to be generated
in HOST1 CKDS. One key, the exporter, is to be used when sending session
keys to HOST2. The other key, the importer, is to be used to decrypt
session keys sent from HOST2.
The complement clear key values
of both the exporter and importer are placed in the ICSF key output
data set. Use these values as the clear key values for the CROSS
statements on HOST2.
- At HOST2 where the PCF/CUSP compatible cryptographic product is
installed, code the appropriate key generation utility program (KGUP)
statement listed below for the environment in HOST2.
- When HOST2 has PCF
CROSS name,KEYLOC=x,KEYREM=y,ADD
- When HOST2 has CUSP
CROSS name,KEYLOC=x,IKEYLOC=xx,KEYREM=y,IKEYREM=yy,ADD
where: - name is the name of HOST1 CDRM.
- x is the key value from HOST1 of the
IMPORTER key.
- y is the key value from HOST1 of the
EXPORTER key.
- xx is the second half of double key
value from HOST1 IMPORTER key.
- yy is the second half of double key
value from HOST1 EXPORTER key.
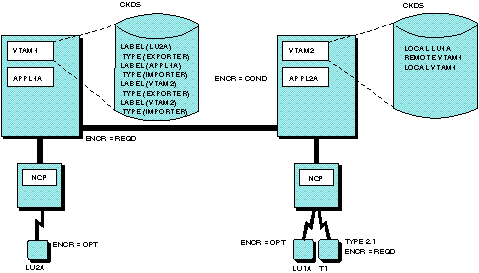
Figure 1 illustrates the possible coding
for cross-domain cryptographic sessions where HOST1 uses ICSF/MVS
and HOST2 uses PCF/CUSP. APPL2A can initiate a cryptographic session
with LU1A. APPL1A can initiate a cryptographic session with LU2A.
APPL2A can initiate a cryptographic session with APPL1A. However,
APPL1A cannot be a PLU in a session with APPL2A because there is no
TYPE(IMPORTER) statement coded in VTAM2, and APPL2A requires cryptography.
Figure 1. Cryptography in multiple-domain environment (Hosts
use different cryptographic services)
For the configuration in Figure 1 to have
any encrypted sessions, start cryptography in both hosts before activating
a session.
 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide
 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide


 Copyright IBM Corporation 1990, 2014
Copyright IBM Corporation 1990, 2014