 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide
 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
Host-by-host cryptography z/OS Communications Server: SNA Network Implementation Guide SC27-3672-01 |
|
|
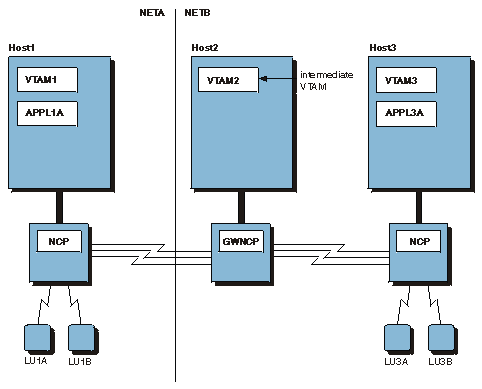
With encryption on a host-by-host basis, each host must support cryptography, and cryptographic key data sets must be filed at each host involved in the LU-LU session initiation. In Figure 1, for cryptographic sessions to exist between resources in VTAM1 and VTAM3, cryptographic key data sets must be filed at VTAM1, VTAM2, and VTAM3. Figure 1. Encryption facility in multiple-network environment

|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |