 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide
 z/OS Communications Server: SNA Network Implementation Guide
z/OS Communications Server: SNA Network Implementation Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
End-to-end cryptography z/OS Communications Server: SNA Network Implementation Guide SC27-3672-01 |
|
|
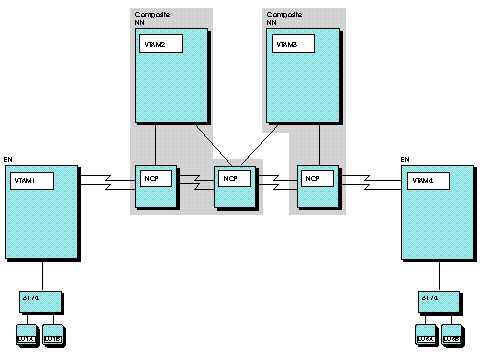
End-to-end cryptography enables an LU-LU session to use encryption as long as all intermediate VTAMs are Version 3 Release 2 or later and both endpoint VTAMs are Version 4 Release 1 or later. Instead of filing cryptographic key data sets at each host that an LU-LU session initiation request traverses, the installation defines the data sets at only the endpoint hosts. These data sets contain the cross keys for the other endpoint and not the adjacent node. Defining cryptographic key data sets between only endpoint hosts eliminates the need to share cryptographic key information with other hosts. This can be important if, for example, the intermediate hosts are owned by a different company. Using end-to-end cryptography in Figure 1, cryptographic key data sets would need to be filed in only VTAM1 and VTAM3. Defining cryptographic keys between only endpoint hosts can still
become burdensome, because many endpoints can exist and the amount
of key definition can get very large. Therefore, in an APPN network,
cryptographic key data sets can be defined in two ways:
Although more key definition is required at a network node server using this strategy, the overall number of cryptographic key data sets declines. End nodes are required to define only one key to the network node server (rather than a key for each node the end node is to communicate with). In addition to the keys for its served end nodes, network node servers are required to define only keys for other network node servers (rather than a key for each node its end nodes are to communicate with). Both session endpoints do not have to use their network node servers for cryptography. That is, one end node can define a key to its server and the server can define a key for the destination end node (instead of defining a key for the destination end node network node server). An example of defining cryptographic keys using the network node server is shown in Figure 1. If VTAM1 files a cryptographic key data set with VTAM2 and VTAM2 files cryptographic key data sets with VTAM4, applications and LUs at VTAM1 can have cryptographic sessions with applications or LUs at VTAM4 without the need for VTAM1 and VTAM4 to exchange keys. Figure 1. Encryption facility in an APPN environment

|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |