Authentication, mapping, and authorization with TFIM V6.1 and TAM
Use IBM® Integration Bus, Tivoli® Federated Identity Manager (TFIM) V6.1, and Tivoli Access Manager (TAM) to control authentication, mapping, and authorization.
IBM Integration Bus makes a single TFIM WS-Trust call for an input node that is configured with a TFIM security profile, which means that a single module chain must be configured to perform all the required authentication, mapping, and authorization operations.
The following diagram shows the configuration of IBM Integration Bus, TFIM, and TAM to enable authentication, mapping, and authorization of an identity in a message flow:
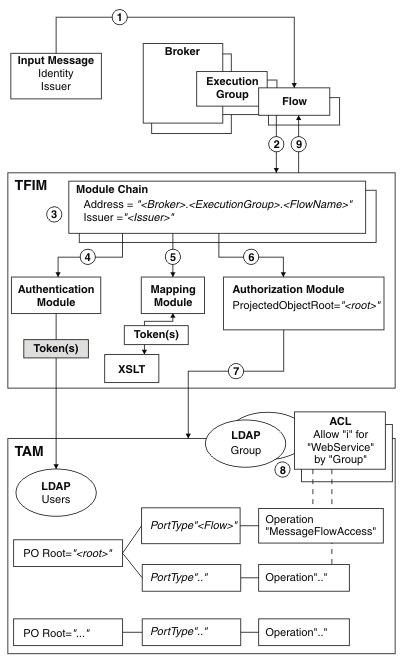
The numbers in the preceding diagram correspond to the following sequence of events:
- A message enters a message flow.
- A WS-Trust request is issued by the integration node, with these
properties:
- RequestType = Validate
- Identity = Token(s) from input message
- Issuer = Issuer from input message
- AppliesTo Address = "Broker.IntegrationServer.FlowName"
- PortType = "FlowName"
- Operation = "MessageFlowAccess"
- TFIM selects a module chain to process the WS-Trust request, based on the AppliesTo Address and Issuer properties of the request.
- A module chain can perform authentication if it includes a module
(such as a UsernameTokenSTSModule or X509STSModule) in
validatemode. - A module chain can perform mapping by using an XSLTransformationModule
in
mappingmode to manipulate the identity information. - A module chain can perform authorization by using an AuthorizationSTSModule
in
othermode. The module chain must be configured with a Protected Object Root value. - The AuthorizationSTSModule performs the authorization check by
making a request to TAM with these properties:
- Action = "i" (invoke)
- Action Group = "WebService"
- Protected Object = "ProtectedObjectRoot.FlowName.MessageFlowAccess"
where "i" and "WebService" are default values used by an AuthorizationSTSModule; and FlowName and MessageFlowAccess are the WS-Trust request PortType and Operation values.
- TAM processes the authorization request by:
- Finding the Access Control Lists (ACLs) associated with protected object "<ProtectedObjectRoot>.<FlowName>.MessageFlowAccess".
- Checking whether or not the ACLs grant action "i" on action group "WebService" to the user (with the user either named directly, or by membership of a named group).
- The WS-Trust reply is returned to the integration node. If this action is the result of a mapping request, the WS-Trust reply contains the mapped identity token.