Authentication, mapping, and authorization with TFIM V6.2 and TAM
You can use IBM® Integration Bus, Tivoli® Federated Identity Manager (TFIM) V6.2, and Tivoli Access Manager (TAM) to control authentication, mapping, and authorization.
IBM Integration Bus makes a single TFIM WS-Trust call for an input node or SecurityPEP node that is configured with a WS-Trust V1.3 STS security profile. As a result, a single module chain must be configured to perform all the required authentication, mapping, and authorization operations.
| Parameter | Value |
|---|---|
| RequestType | The type of request issued to the trust service. Valid values are: |
| Issuer | This value is determined by the effective setting of the IssuedBy property on the Basic tab of the SecurityPEP node or the Security tab of the input node. |
| AppliesTo | This value is determined by the type of node: |
This section describes an authorization configuration that you can use to perform the authorization operation with TFIM V6.2 and TAM.
In the security profile, set the TFIM V6.2 endpoint for the authorization operation. When you create a module chain to be used by a security enabled input node or SecurityPEP node, and resolved by AppliesTo information, you must include the TFIM TAMAuthorizationSTModule to invoke TAM authorization.
The TAM Access Control List (ACL), which determines the authorization decision, is located in the TAM protected object space using the path that is set on the ObjectName attribute of the TFIM STS universal user context input to the TAMAuthorizationSTSModule module.
The following diagram shows the configuration of IBM Integration Bus, TFIM V6.2, and TAM to enable authentication, mapping, and authorization of an identity in a message flow:
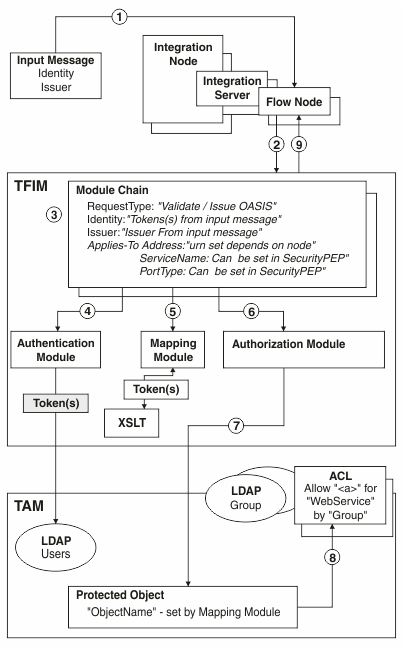
- A message enters a message flow.
- A WS-Trust request is issued by the integration node, with the RequestType, Issuer, and AppliesTo properties set.
- TFIM selects a module chain to process the WS-Trust request, based on the RequestType, Issuer, and AppliesTo properties of the request.
- A module chain can perform authentication if it includes a module in Validate mode that is appropriate to the token type that is being passed in the request from the message flow input message. For example, a Username and Password token can be authenticated using a UsernameTokenSTSModule .
- The module chain must perform some mapping by using an XSLTransformationModule in mapping mode to manipulate the identity information and to provide the required context attributes in the TFIM stsuser object for use by subsequent modules.
- A module chain can perform authorization in TAM by using the TAMAuthorizationSTSModule.
- The TAMAuthorizationSTSModule performs the authorization check
by making a request to TAM with these properties:
- Action = a (where a is the
stsuser context action attribute). For example, x for
eXecute could be set using the following code:
<stsuuser:ContextAttributes> <!-- Action --> <stsuuser:Attribute name="Action" type="urn:ibm:names:ITFIM:stsmodule:tamazn"> <stsuuser:Value>x</stsuuser:Value> </stsuuser:Attribute> </stsuuser:ContextAttributes> - Action Group = WebService
- Protected Object = ProtectedObjectName (where ProtectedObjectName is
the stsuser context action attribute). For example, x for
eXecute could be set using the following code:
Typically, ProtectedObjectName is set conditionally from the AppliesTo information in the request.<stsuuser:ContextAttributes> <!-- ObjectName --> <stsuuser:Attribute name="ObjectName" type="urn:ibm:names:ITFIM:stsmodule:tamazn"> <stsuuser:Value>ProtectedObjectName</stsuuser:Value> </stsuuser:Attribute> </stsuuser:ContextAttributes>
- Action = a (where a is the
stsuser context action attribute). For example, x for
eXecute could be set using the following code:
- TAM processes the authorization request by:
- Finding the Access Control Lists (ACLs) associated with protected object ProtectedObjectName
- Checking whether the ACLs grant action a on action group WebService to the user (the user is named either directly or indirectly, through membership of a named group).
- The WS-Trust reply is returned to the integration node. If this action is the result of a mapping request, the WS-Trust reply contains the mapped identity token.