IBM Business Process Manager security overview
IBM® Business Process Manager is based on Java™ Platform, Enterprise Edition (Java EE) and is delivered largely through HTTP protocols. As a result, IBM Business Process Manager has the same security requirements as any other Java EE application.
IBM Business Process Manager defines a fine-grained authorization model that uses groups, roles, and teams.
Groups
Groups are collections of users. Being a member of a group does not grant a user any specific permission. Users are added to the collection, which simplifies administration by allowing administrators to assign the entire collection of users within the group to a role instead of having to manage long lists of users individually. IBM Business Process Manager default security groups are an exception; permissions are associated with membership in these configurable groups. Refer to the IBM Business Process Manager default group types topic for more details and a list of the IBM Business Process Manager default groups, including their corresponding descriptions.Roles
Roles are a logical application level construct that divides the user population in to multiple classes of users. For example, in a website shopping application, you might have the following roles:- Administrators
- Catalog managers
- Customers
- Anonymous
Different roles can be assigned different levels of security, and the security access of individuals, or groups of individuals, can be controlled by assigning them to specific roles.
- WebSphere® Application Server administrative roles. See Administrative roles.
- IBM Business Process Manager application Java EE roles. See IBM Business Process Manager application J2EE roles.
- IBM Business Process Manager security roles that allow configuring system accounts. See IBM Business Process Manager roles.
Teams
Teams are used to define groups of users who can perform tasks. A team can either be defined as a static list of users and groups, or be defined dynamically by a service. You can assign a team of managers to each team to define which people in the organization can perform managerial actions for the team. Teams have aspects of both groups and roles. As tasks are assigned to teams, a user is granted access to a task by adding the user to the team. Teams with statically defined members are a collection of users, which is similar to a group. Unlike groups, teams have the concept of team managers.| Task | Interface | To learn more |
|---|---|---|
| Granting access to the repository | Process Center Console | See Managing access to the Process Center repository. |
| Binding users to teams during process development | Designer in Process Designer | See Creating a team. |
| Defining who has managerial authority over a team | Designer in Process Designer | See Defining team managers. |
| Using services to define dynamic teams | Designer in Process Designer | See Using services to define dynamic teams. |
| Assigning an activity to a team | Designer in Process Designer | See Assigning teams to BPD activities. |
| Adding users and groups from an external provider to IBM BPM security groups | Process Admin Console | See Creating and managing groups. |
| Modifying existing teams at run time | Process Admin Console | See Configuring runtime teams. |
User registry
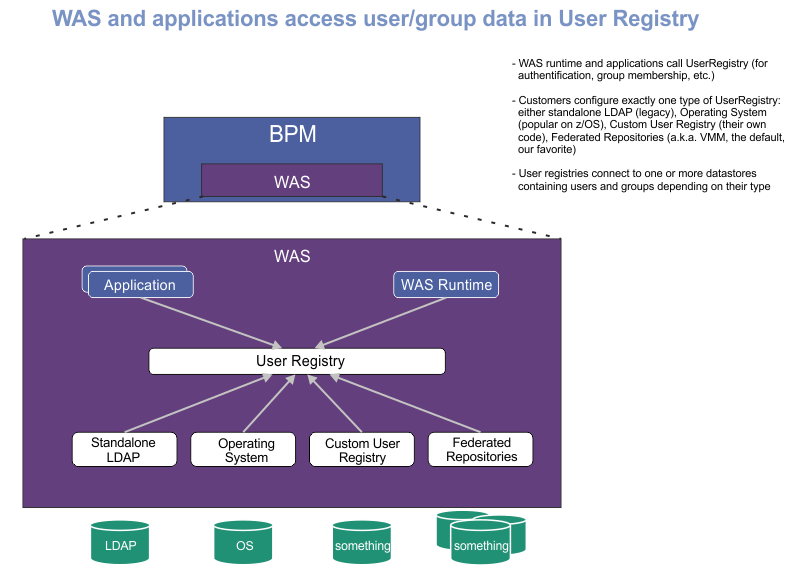
IBM Business Process Manager authorization relies on users and groups that are defined in the user registry. A user registry is an architectural layer that manages users and groups in WebSphere Application Server. LDAP servers are the most commonly used source of user and group data storage. Although IBM Business Process Manager can utilize a stand-alone LDAP registry, you should use a federated repository configuration that can comprise multiple LDAP repositories. For more information, see Authentication of users in IBM Business Process Manager.
IBM Business Process Manager does not lock user accounts after a configurable number of failed authentication attempts. End user accounts are managed in a user repository (typically LDAP connected to Federated Repositories). IBM Business Process Manager is just one of many client systems to the user repository. The user repository is the system of records for the user accounts and therefore defines rules such as password lock policy. For IBM Tivoli Directory Server, you can read more about password policies at http://www.ibm.com/developerworks/tivoli/library/t-tdspp-ect/.
The following diagram illustrates how WebSphere Application Server and applications access user and group data in the user registry.
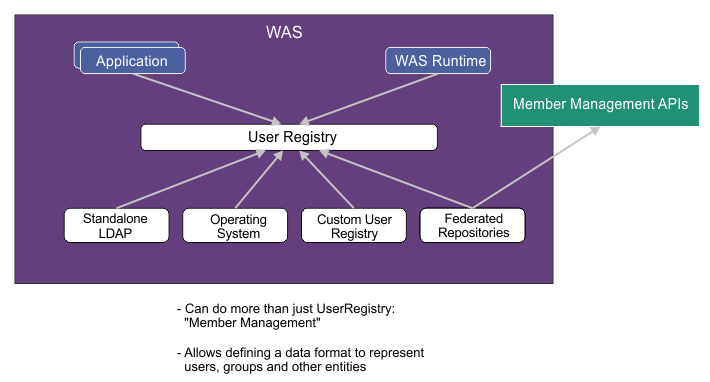
The following diagram illustrates how the user registry works for member management APIs.