Customization
JSSE includes a standard implementation that can be customized by plugging in different implementations or specifying the default keystore, and so on. The following tables summarize which aspects can be customized, what the defaults are, and which mechanisms are used to provide customization.
Some of the customizations are done by setting system property or security property values. Sections following the table explain how to set such property values.
The following table shows items that are customized by setting a
java.security.Security property:
| Security Property | Customized Item | Default Value | Notes |
|---|---|---|---|
JCE encryption algorithms used by the IBMJSSE2 provider |
Give alternative JCE algorithm providers a higher preference order than the IBMJCE provider; see Customizing the Encryption Algorithm Providers. | IBMJCE implementations | None |
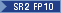
jdk.certpath.disabledAlgorithms1 |
Disabled certificate verification cryptographic algorithm (see Disabled and restricted cryptographic algorithms) | MD2,
RSA keySize < 1024, |
None |
jdk.tls.disabledAlgorithms1 |
Disabled and restricted cryptographic algorithms | SSLv3, |
Disables specific algorithms (protocols versions, cipher suites, key exchange mechanisms,
etc.) that will not be negotiated for Transport Layer Security (TLS) connections, even if they are
enabled explicitly in an application. Note: If you are using the IBMJCEFIPS provider
for TLS, add
RSASSA-PSS, RSAPSS to this system property in the
java.security
file. |
 jdk.tls.keyLimits1 |
 Limiting the amount of data that algorithms can encrypt with a set of keys Limiting the amount of data that algorithms can encrypt with a set of keys |
 AES/GCM/NoPadding KeyUpdate 2^37 AES/GCM/NoPadding KeyUpdate 2^37 |
 Limits the amount of data an algorithm may encrypt with a specific set of keys; once this
limit is reached, a KeyUpdate post-handshake message is sent, which requests that the current set of
keys be updated. Limits the amount of data an algorithm may encrypt with a specific set of keys; once this
limit is reached, a KeyUpdate post-handshake message is sent, which requests that the current set of
keys be updated. |
 jdk.tls.legacyAlgorithms1 |
 Legacy algorithms Legacy algorithms |
 K_NULL, C_NULL, M_NULL, DH_anon, ECDH_anon, RC4_128, RC4_40, DES_CBC, DES40_CBC,
3DES_EDE_CBC2 |
 Specifies which algorithms are considered legacy algorithms, which are not negotiated during
TLS security parameters negotiation unless there are no other candidates. Specifies which algorithms are considered legacy algorithms, which are not negotiated during
TLS security parameters negotiation unless there are no other candidates. |
 jdk.tls.maxCertificateChainLength1 |
 Certificate chain handling Certificate chain handling |
 10 10 |
 Specifies the maximum allowed length of the certificate chain in TLS/DTLS
handshaking. Specifies the maximum allowed length of the certificate chain in TLS/DTLS
handshaking. |
 jdk.tls.maxHandshakeMessageSize1 |
 Certificate chain handling Certificate chain handling |
 32768 (32 kilobytes) 32768 (32 kilobytes) |
 Specifies the maximum allowed size, in bytes, for the handshake message in TLS/DTLS
handshaking. Specifies the maximum allowed size, in bytes, for the handshake message in TLS/DTLS
handshaking. |
jdk.tls.rejectClientInitiatedRenegotiation1 |
Rejects client-initiated renegotiation on the server side. If this system property is
true, then the server will not accept client initiated renegotiation and will fail
with a fatal handshake_failure alert. |
false |
None |
 jdk.tls.server.defaultDHEParameters1 |
 Diffie-Hellman groups Diffie-Hellman groups |
 Safe prime Diffie-Hellman groups in JDK TLS implementation Safe prime Diffie-Hellman groups in JDK TLS implementation |
 Defines default finite field Diffie-Hellman ephemeral (DHE) parameters for TLS
processing Defines default finite field Diffie-Hellman ephemeral (DHE) parameters for TLS
processing |
ocsp.enable1 |
Determine X.509 certificate revocation status with OCSP | false |
Enables client-driven Online Certificate Status Protocol (OCSP). You must also enable revocation checking; see Setting up a Java Client to use Client-Driven OCSP. |
security.provider.n |
Cryptographic service provider; see Customizing the Provider Implementation and Customizing the Encryption Algorithm Providers | Differs per platform; check the java.security security properties file. | Specify the provider in the security.provider.n= line in
the security properties file, where n is an integer whose value is equal or
greater than 1. |
ssl.KeyManagerFactory.algorithm |
Default key manager factory algorithm name (see Customizing the Default Key and Trust Managers) | IbmX509 |
None |
ssl.ServerSocketFactory.provider1 |
Default SSLServerSocketFactory implementation |
SSLServerSocketFactory implementation from IBM: com.ibm.jsse2.SSLServerSocketFactoryImpl | None |
ssl.SocketFactory.provider1 |
Default SSLSocketFactory implementation |
SSLSocketFactory implementation from IBM: com.ibm.jsse2.SSLSocketFactoryImpl | None |
ssl.TrustManagerFactory.algorithm |
Default trust manager factory algorithm name (see Customizing the Default Key and Trust Managers) | PKIX |
None |
1 There is no guarantee the property will continue to exist or be of the same type (system or security) in future releases.
2 The list of restricted, disabled, and legacy algorithms
specified in these security properties might change; see the java.security file in
your SDK installation for the latest values.
java.lang.System property.
| System Property | Customized Item | Default | Notes |
|---|---|---|---|
 com.ibm.jsse2.allowLegacyHelloMessages |
 Transport Layer Security (TLS) Renegotiation Issue Transport Layer Security (TLS) Renegotiation Issue |
 true |
 If If true, then allow the peer to handshake without requiring the proper RFC
5746 messages. |
 com.ibm.jsse2.allowUnsafeRenegotiation |
 Transport Layer Security (TLS) Renegotiation Issue Transport Layer Security (TLS) Renegotiation Issue |
 false |
 If If true, then permit full (unsafe) legacy negotiation. |
com.ibm.jsse2.checkRevocation1 |
Revocation checking | false |
You must enable revocation checking to enable client-driven OCSP; see Determine X.509 certificate revocation status with OCSP. |
com.ibm.jsse2.disableSSLv31 |
Padding Oracle On Downgraded Legacy Encryption (POODLE) security vulnerability | true |
Disables use of the SSL V3.0 protocol, which is the default. Setting this value to
false enables SSL V3.0 and exposes an application to this vulnerability. |
 com.ibm.jsse2.sslEngineCloseNotifyReceive |
 Whether to throw an SSLException on an
SSLEngine.closeInbound() method call if the engine did not receive the proper
SSL/TLS close notification from the peer Whether to throw an SSLException on an
SSLEngine.closeInbound() method call if the engine did not receive the proper
SSL/TLS close notification from the peer |
 true |

When the value of the property is Set this property to  |
 com.ibm.jsse2.overrideDefaultCSName |
 Whether to return cipher suite names that match Oracle equivalents Whether to return cipher suite names that match Oracle equivalents |
 false |

Set this property to Set this property to  |
com.ibm.jsse2.sp800-1311 |
SP800-131A Compliance | off |
Set this property to transition to specify that SP800-131a transition
compliance is requested. Set the property to strict to allow only strict adherence
to the SP800-131a recommendation. The default value specifies not SP800-131a compliant. |
 com.ibm.jsse2.strictServerSigCheck
1 |
 Whether to strictly enforce RFC 5246 - TLS 1.2 Section 7.4.1.4.1. Signature Algorithms on the
entire certificate chain that the server presented or not. Whether to strictly enforce RFC 5246 - TLS 1.2 Section 7.4.1.4.1. Signature Algorithms on the
entire certificate chain that the server presented or not. |
 false |

Set this property to Set this property to  |
com.ibm.jsse2.suiteB1 |
Suite B compliance, see Suite B Profile for Transport Layer Security (TLS) | false |
Set this property to 128 to specify the 128-bit minimum level of security,
or 192 to specify the 192-bit minimum level of security. The default value
specifies not Suite B compliant. |
com.ibm.jsse2.usefipsprovider1 |
Run IBMJSSE2 in FIPS mode | false |
Set this property to true to run IBMJSSE2 in FIPS mode. |
Customize via port field in the HTTPS URL1 |
Default HTTPS port | 443 |
None |
https.cipherSuites1 |
Default cipher suites for HTTPS connections | Determined by the socket factory. | This contains a comma-separated list of cipher suite names specifying which cipher suites to
enable for use on this HttpsURLConnection. See the SSLSocket
setEnabledCipherSuites(String[]) method. Note that this method sets the preference order
of the ClientHello cipher suites directly from the String array passed to
it. |
https.protocols1 |
Default handshaking protocols for HTTPS connections. See
also Enabling TLS 1.3 See
also Enabling TLS 1.3 |
Determined by the socket factory. | This contains a comma-separated list of protocol suite names specifying which protocol suites
to enable on this HttpsURLConnection. See the SSLSocket
setEnabledProtocols(String[]) method. |
https.proxyHost1 |
Default proxy host | None | None |
https.proxyPort1 |
Default proxy port | 80 |
None |
java.protocol.handler.pkgs |
Specifying an Alternative HTTPS Protocol Implementation | Implementation from IBM com.ibm.net.ssl.www2.protocol |
None |
javax.net.ssl.keyStore1 |
Default keystore; see Customizing the Default Key and Trust Stores, Store Types, and Store Passwords | If no system property, then jssecacerts is the default. Otherwise,
cacerts is the default. |
The value NONE may be specified. This setting is appropriate if the keystore
is not file-based (for example, it resides in a hardware token) |
javax.net.ssl.keyStorePassword1 |
Default keystore password; see Customizing the Default Key and Trust Stores, Store Types, and Store Passwords | changeit |
It is inadvisable to specify the password in a way that exposes it to discovery by other users. For example, specifying the password on the command line. To keep the password secure, have the application prompt for the password, or specify the password in a properly protected option file. |
javax.net.ssl.keyStoreProvider1 |
Default keystore provider; see Customizing the Default Key and Trust Stores, Store Types, and Store Passwords | None | None |
javax.net.ssl.keyStoreType1 |
Default keystore type; see Customizing the Default Key and Trust Stores, Store Types, and Store Passwords | KeyStore.getDefaultType() |
None |
javax.net.ssl.sessionCacheSize |
Default value for the maximum number of entries in the SSL session cache | 100 |
The session cache size can be set by calling the
SSLSessionContext.setSessionCacheSize method or by setting the
javax.net.ssl.sessionCachSize system property. If the cache size is not set, the
default value is used. |
javax.net.ssl.trustStore1 |
Default truststore; see Customizing the Default Key and Trust Stores, Store Types, and Store Passwords | jssecacerts, if it exists; otherwise, cacerts |
None |
javax.net.ssl.trustStorePassword1 |
Default truststore password; see Customizing the Default Key and Trust Stores, Store Types, and Store Passwords | None | It is inadvisable to specify the password in a way that exposes it to discovery by other users. For example, specifying the password on the command line. To keep the password secure, have the application prompt for the password, or specify the password in a properly protected option file. |
javax.net.ssl.trustStoreProvider1 |
Default truststore provider; see Customizing the Default Key and Trust Stores, Store Types, and Store Passwords | None | None |
javax.net.ssl.trustStoreType1 |
Default truststore type; see Customizing the Default Key and Trust Stores, Store Types, and Store Passwords | KeyStore.getDefaultType() |
The value NONE may be specified. This setting is appropriate if the
truststore is not file-based (for example, it resides in a hardware token). |
 jdk.tls.acknowledgeCloseNotify1
 |
 Specifying that a close_notify alert is sent when one is received Specifying that a close_notify alert is sent when one is received |
 false |
 If the system property is set to If the system property is set to true, then when the client or server
receives a close_notify alert, it sends a corresponding close_notify alert and the connection is
duplex-closed. |
 jdk.tls.client.cipherSuites1 |
 Client-side default enabled cipher suites; see Specifying default enabled cipher suites. Client-side default enabled cipher suites; see Specifying default enabled cipher suites. |
 See Cipher suites for a list of currently implemented IBMJSSE2 cipher
suites, sorted by order of preference. See Cipher suites for a list of currently implemented IBMJSSE2 cipher
suites, sorted by order of preference. |

Attention: These system properties can be used to configure weak cipher suites, or the
configured cipher suites might be weak in the future. It is not recommended that you use these
system properties without understanding the risks.
 |
 jdk.tls.client.enableCAExtension |
 Enables certificate authorities extension for server certificate selection. Enables certificate authorities extension for server certificate selection. |
 false |
 The certificate authorities extension, an optional extension introduced in TLS 1.3, is used to
indicate the certificate authorities (CAs) that an endpoint supports and that should be used by the
receiving endpoint to guide certificate selection. This extension is always present for client
certificate selection but is optional for server certificate selection; to enable it, set the system
property to The certificate authorities extension, an optional extension introduced in TLS 1.3, is used to
indicate the certificate authorities (CAs) that an endpoint supports and that should be used by the
receiving endpoint to guide certificate selection. This extension is always present for client
certificate selection but is optional for server certificate selection; to enable it, set the system
property to true. Notes:
 |
 jdk.tls.client.enableStatusRequestExtension1 |
 Setting up a Java Client to Use OCSP Stapling Setting up a Java Client to Use OCSP Stapling |
 false |
 If If true, then the status_request and status_request_v2 extensions are
enabled, and processing for CertificateStatus messages sent by the server is
enabled. |
 jdk.tls.client.disableExtensions1 |
 Configuring Default Extensions Configuring Default Extensions |
 None |
 Blocks extensions used on the client side. Blocks extensions used on the client side. |
jdk.tls.client.protocols1 |
Default handshaking protocols for TLS clients. See Protocols and Enabling TLS 1.3 and Enabling TLS 1.3 . . |
none |
To enable specific IBMJSSE2 protocols on the client, specify them in a
comma-separated list within quotation marks; all other supported protocols are not enabled on the
client. For example, if jdk.tls.client.protocols="TLSv1,TLSv1.1", the default
protocol settings on the client for TLSv1 and TLSv1.1 are enabled, while SSLv3, TLSv1.2, and TLSv1.3 are not enabled. |
 jdk.tls.client.SignatureSchemes1 |
 Contains
a comma-separated list of supported signature scheme names that specifies the signature schemes that
could be used for TLS connections on the client side. Contains
a comma-separated list of supported signature scheme names that specifies the signature schemes that
could be used for TLS connections on the client side. |
 None None |
 Unrecognized or unsupported signature scheme names specified in the property are ignored. If
this system property is not defined or empty, the provider-specific default is used. The names are
not case sensitive. Unrecognized or unsupported signature scheme names specified in the property are ignored. If
this system property is not defined or empty, the provider-specific default is used. The names are
not case sensitive. |
jdk.tls.ephemeralDHKeySize1 |
Customizing the size of Ephemeral Diffie-Hellman Keys | |
None |
 jdk.tls.namedGroups1 |
 Customizing the supported named groups for TLS key exchange. Customizing the supported named groups for TLS key exchange. |
 If this system property is not defined or the value is empty, the default groups and
preferences will be used. For more information about the default groups, see Setting a list of enabled named groups. If this system property is not defined or the value is empty, the default groups and
preferences will be used. For more information about the default groups, see Setting a list of enabled named groups. |
 This contains a comma-separated list within quotation marks of enabled named groups in
preference order. For example: This contains a comma-separated list within quotation marks of enabled named groups in
preference order. For example: jdk.tls.namedGroups="secp521r1,secp256r1 |
 jdk.tls.server.cipherSuites1 |
 Server-side default enabled cipher suites. See Specifying default enabled cipher suites. Server-side default enabled cipher suites. See Specifying default enabled cipher suites. |
 See Cipher suites to determine which cipher suites are enabled by
default See Cipher suites to determine which cipher suites are enabled by
default |

Attention: These system properties can be used to configure weak cipher suites, or the
configured cipher suites may be weak in the future. It is not recommended that you use these system
properties without understanding the risks.
 |
 jdk.tls.server.enableStatusRequestExtension1 |
 Setting Up a Java Server to Use OCSP Stapling Setting Up a Java Server to Use OCSP Stapling |
 false |
 If If true, then server-side support for OCSP stapling is enabled |
 jdk.tls.server.disableExtensions1 |
 Configuring Default Extensions Configuring Default Extensions |
 None None |
 Blocks extensions used on the server side. Blocks extensions used on the server side. |
 jdk.tls.server.protocols1 |
 Default handshaking protocols for TLS servers. See Protocols and Enabling TLS 1.3. Default handshaking protocols for TLS servers. See Protocols and Enabling TLS 1.3. |
 none |
 To configure the default enabled protocol suite in the server side of an To configure the default enabled protocol suite in the server side of an
IBMJSSE2 provider, specify the protocols in a comma-separated list within quotation
marks. The protocols in this list are standard SSL protocol names as described in Appendix A: Standard Names. Note that this system property impacts only the default
protocol suite (SSLContext of the algorithms SSL and TLS). If an application uses
a version-specific SSLContext (SSLv3, TLSv1, TLSv1.1, TLSv1.2, or TLSv1.3), or
sets the enabled protocol version explicitly, this system property has no impact. |
 jdk.tls.server.SignatureSchemes1 |
 Contains a comma-separated list of supported signature scheme names that specifies the
signature schemes that could be used for TLS connections on the server side. Contains a comma-separated list of supported signature scheme names that specifies the
signature schemes that could be used for TLS connections on the server side. |
 None None |
 Unrecognized or unsupported signature scheme names specified in the property are ignored. If
this system property is not defined or empty, then the provider-specific default is used. The names
are not case sensitive. Unrecognized or unsupported signature scheme names specified in the property are ignored. If
this system property is not defined or empty, then the provider-specific default is used. The names
are not case sensitive. |
jsse.enableCBCProtection1 |
Adds randomness to prevent CBC attacks. For more information, see Browser Exploit Against SSL/TLS (BEAST) security vulnerability. |
|
Set this property to true to specify that CBC protection is enabled. |
 jsse.enableFFDHE |
 Enables or disables Finite Field Diffie-Hellman Ephemeral (FFDHE) parameters for TLS key
exchange. Enables or disables Finite Field Diffie-Hellman Ephemeral (FFDHE) parameters for TLS key
exchange. |
 true |
 FFDHE is a TLS extension defined in RFC 7919.
This extension enables TLS connections to use known finite field Diffie-Hellman groups. Some very
old TLS vendors might be unable to handle TLS extensions. In this case, set this property to FFDHE is a TLS extension defined in RFC 7919.
This extension enables TLS connections to use known finite field Diffie-Hellman groups. Some very
old TLS vendors might be unable to handle TLS extensions. In this case, set this property to
false to disable the FFDHE extension. |
 jsse.enableMFLNExtension1 |
 Customizing the Maximum Fragment Length Negotiation (MFLN) extension Customizing the Maximum Fragment Length Negotiation (MFLN) extension |
 false |
 None None |
jsse.enableSNIExtension1 |
Server Name Indication option | true |
Server Name Indication (SNI) is a TLS extension, defined in RFC 6066. It enables TLS connections to virtual servers, in
which multiple servers for different network names are hosted at a single underlying network
address. Some very old TLS vendors might not be able handle TLS extensions. In this case, set this
property to false to disable the SNI extension |
jsse.SSLEngine.acceptLargeFragments1 |
Default sizing buffers for large TLS packets | None | Setting this system property to true, SSLSession will size buffers to handle
large data packets by default (see the note in SSLSession and ExtendedSSLSession Interfaces). This might cause
applications to allocate unnecessarily large SSLEngine buffers. Instead,
applications should dynamically check for buffer overflow conditions and resize buffers as
appropriate (see Status of Operations). |
1 There is no guarantee the property will continue to exist or be of the same type (system or security) in future releases.
 MD5,
MD5,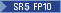 SHA1 jdkCA & usage TLSServer,
SHA1 jdkCA & usage TLSServer, 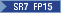 include jdk.disabled.namedCurves
include jdk.disabled.namedCurves RC4,
RC4,  DES,
DES, 3DES_EDE_CBC,
DESede,
3DES_EDE_CBC,
DESede, anon, NULL,
anon, NULL, 2048
2048