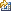Describes the syntax and attributes of the TCPIPSERVICE resource.
>>-TCPIPSERVICE(name)--GROUP(groupname)-------------------------> .-BACKLOG(0)-------. >--+-------------------+--+------------------+------------------> '-DESCRIPTION(text)-' '-BACKLOG(backlog)-' .-GRPCRITICAL(NO)--. >--+--------------------+--+------------------+-----------------> '-DNSGROUP(dnsgroup)-' '-GRPCRITICAL(YES)-' .-HOST(ANY)-------------. >----+-----------------------+----PORTNUMBER(port)--------------> +-HOST(DEFAULT)---------+ +-HOST(hostname)--------+ +-IPADDRESS(ANY)--------+ +-IPADDRESS(DEFAULT)----+ +-IPADDRESS(INADDR_ANY)-+ '-IPADDRESS(ipaddress)--' .-PROTOCOL(HTTP)--| Attributes used with PROTOCOL(HTTP) |-. >--+---------------------------------------------------------+--> +-PROTOCOL(ECI)--| Attributes used with PROTOCOL(ECI) |---+ +-PROTOCOL(IPIC)--| Attributes used with PROTOCOL(IPIC) |-+ '-PROTOCOL(USER)--| Attributes used with PROTOCOL(USER) |-' .-STATUS(OPEN)---. >--+----------------+------------------------------------------>< '-STATUS(CLOSED)-' Attributes used with PROTOCOL(ECI) .-ATTACHSEC(LOCAL)--. |--+--------------------+--+-------------------+----------------> '-DNSGROUP(dnsgroup)-' '-ATTACHSEC(VERIFY)-' .-SOCKETCLOSE(NO)-. .-TRANSACTION(CIEP)--------. >--+-----------------+--+--------------------------+------------| '-TRANSACTION(transaction)-' Attributes used with PROTOCOL(HTTP) |--+--------------------+---------------------------------------> '-DNSGROUP(dnsgroup)-' .-AUTHENTICATE(NO)--------. .-SSL(NO)-----------------------------------------------------. >--+-+-------------------------+--+-------------------------------------------------------------+-+--> | +-AUTHENTICATE(AUTOMATIC)-+ '-+-SSL(YES)--------+--+--------------------+--CIPHERS(value)-' | | '-AUTHENTICATE(BASIC)-----' '-SSL(CLIENTAUTH)-' '-CERTIFICATE(label)-' | '-+-AUTHENTICATE(AUTOREGISTER)-+--SSL(CLIENTAUTH)--+--------------------+--CIPHERS(value)------' '-AUTHENTICATE(CERTIFICATE)--' '-CERTIFICATE(label)-' .-SOCKETCLOSE(NO)-----. >--+---------------+--+---------------------+-------------------> '-REALM(string)-' '-SOCKETCLOSE(hhmmss)-' .-MAXDATALEN(32)-----. .-MAXPERSIST(NO)-----. >--+--------------------+--+--------------------+---------------> '-MAXDATALEN(number)-' '-MAXPERSIST(number)-' .-TRANSACTION(CWXN)--------. >--+--------------------------+--+-------------------+----------> '-TRANSACTION(transaction)-' '-TSQPREFIX(prefix)-' .-URM(DFHWBAAX)-----. >--+-------------------+----------------------------------------| '-URM(program_name)-' Attributes used with PROTOCOL(IPIC) .-SSL(NO)-----------------------------------------------------. |----+-------------------------------------------------------------+----> '-+-SSL(YES)--------+--+--------------------+--CIPHERS(value)-' '-SSL(CLIENTAUTH)-' '-CERTIFICATE(label)-' .-SOCKETCLOSE(NO)-. .-TRANSACTION(CISS)--------. >--+-----------------+--+--------------------------+------------> '-TRANSACTION(transaction)-' .-URM(DFHISAIP)-----. >--+-------------------+----------------------------------------| +-URM(NO)-----------+ '-URM(program_name)-' Attributes used with PROTOCOL(USER) |--+--------------------+---------------------------------------> '-DNSGROUP(dnsgroup)-' .-AUTHENTICATE(NO)--------. .-SSL(NO)-----------------------------------------------------. >--+-+-------------------------+--+-------------------------------------------------------------+-+--> | +-AUTHENTICATE(AUTOMATIC)-+ '-+-SSL(YES)--------+--+--------------------+--CIPHERS(value)-' | | '-AUTHENTICATE(BASIC)-----' '-SSL(CLIENTAUTH)-' '-CERTIFICATE(label)-' | '-+-AUTHENTICATE(AUTOREGISTER)-+--SSL(CLIENTAUTH)--+--------------------+--CIPHERS(value)------' '-AUTHENTICATE(CERTIFICATE)--' '-CERTIFICATE(label)-' .-SOCKETCLOSE(NO)-----. .-MAXDATALEN(32)-----. >--+---------------------+--+--------------------+--------------> '-SOCKETCLOSE(hhmmss)-' '-MAXDATALEN(number)-' .-TRANSACTION(CWXU)--------. >--+--------------------------+--+-------------------+----------> '-TRANSACTION(transaction)-' '-TSQPREFIX(prefix)-' >--URM(program)-------------------------------------------------|
- ATTACHSEC({LOCAL|VERIFY})
- Specifies the level of attach-time user security that is required
for this connection.
This option is valid only for PROTOCOL(ECI).
- AUTHENTICATE({NO|ASSERTED|AUTOMATIC|AUTOREGISTER|BASIC|CERTIFICATE})
- Specifies the authentication and identification scheme to be used
for inbound TCP/IP connections for the HTTP and USER protocols. For
the IPIC protocol, this attribute is not applicable. For the ECI protocol,
this attribute is invalid. For more information about authentication,
see Identification and authentication.
- ASSERTED
- The ASSERTED attribute in TCPIPSERVICE definitions is obsolete but is retained for compatibility reasons.
When PROTOCOL(HTTP) or PROTOCOL(USER) is specified:- NO
- The client is not required to send authentication or identification information. However, if the client sends a valid certificate that is already registered to the security manager, and associated with a user ID, then that user ID identifies the client.
- BASIC
- HTTP Basic authentication
is used to obtain a user ID, and password or password phrase from the client.
If the client has sent an Authorization header, its contents are decoded as a user ID and password or password phrase. If these are not valid, an HTTP 401 response is returned, together with a WWW-Authenticate header, which causes the client program to prompt the user for a new user ID and password or password phrase. This process continues until the client either supplies a valid user ID, and password or password phrase, or cancels the connection.
When the user is successfully authenticated, the user ID supplied identifies the client.
- AUTOREGISTER
- SSL client certificate authentication is used to authenticate
the client.
- If the client sends a valid certificate that is already registered to the security manager and associated with a user ID, then that user ID identifies the client.
- If the client sends a valid certificate that is not registered to the security manager, then HTTP Basic authentication is used to obtain a user ID and password or password phrase from the client. If the password or password phrase is valid, CICS registers the certificate with the security manager and associates it with the user ID. The user ID identifies the client.
- For a certificate to be registered, the client needs the appropriate access definition in RACF®. The access that is required is READ access to the IRR.DIGTCERT.ADD profile in the FACILITY class.
Note: If you specify AUTHENTICATE(AUTOREGISTER), you must also specify SSL(CLIENTAUTH). - AUTOMATIC
- This function combines the AUTOREGISTER and BASIC functions.
- If the client sends a certificate, then processing will continue as described in AUTOREGISTER.
- If the client does not send a certificate, then processing will proceed as described in BASIC.
- CERTIFICATE
- SSL client certificate authentication is used to authenticate
and identify the client. The client must send a valid certificate
that is already registered to the security manager, and associated
with a user ID. If a valid certificate is not received, or the certificate
is not associated with a user ID, the connection is rejected.
When the user has been successfully authenticated, the user ID associated with the certificate identifies the client.
Note: If you specify AUTHENTICATE(CERTIFICATE), you must also specify SSL(CLIENTAUTH).
Note: For the HTTP or USER protocol, the analyzer program (named by the user replaceable module (URM) attribute) can change the user ID supplied by the authentication process. If the authentication process does not supply a user ID, the analyzer program or URIMAP definition can supply one. Otherwise, the CICS default user ID is used. - BACKLOG(0|backlog)
- Specifies, in the range 1 - 32767, the maximum number of inbound TCP/IP connection open requests that can be queued in TCP/IP waiting for CICS processing. When the maximum is reached, TCP/IP rejects additional requests. If the value of BACKLOG is zero, the value of TCP/IP attribute SOMAXCONN is used. If the value of BACKLOG is greater than SOMAXCONN, the value of SOMAXCONN is used. For IPIC connections set this value to the maximum number of concurrent connection requests that can be established by using this TCPIPSERVICE.
- CERTIFICATE(label)
- Specifies the label of an X.509 certificate that is used as a
server certificate during the SSL handshake when the connection is
acquired. If this attribute is omitted, the default certificate that
is defined in the key ring for the CICS region
user ID is used.
Certificate labels can be up to 32 bytes long.
The certificate must be stored in a key ring in the database of the external security manager. For more information, see Building a key ring.
This attribute cannot be specified unless SSL(YES) or SSL(CLIENTAUTH) is also specified.
- CIPHERS(value)
-
 The
CIPHERS attribute can be specified in either of two ways:
The
CIPHERS attribute can be specified in either of two ways:- A string of up to 56 hexadecimal digits that is interpreted as a list of up to 28 2-digit cipher suite codes.
- The name of the SSL cipher suite specification file, which is a z/OS® UNIX file in the security/ciphers subdirectory of the directory that is specified by the USSCONFIG system initialization parameter. For example if USSCONFIG is set to /var/cicsts and CIPHERS is set to strongciphers.xml, the fully qualified file name is /var/cicsts/security/ciphers/strongciphers.xml. For more information, see SSL cipher suite specification file.
 When you use the CEDA transaction to define the resource, CICS automatically initializes the attribute with a default list of acceptable codes. For CICS to initialize the attribute, the KEYRING system initialization parameter must be specified in the CICS region where you are running CEDA. If KEYRING is not set, CICS does not initialize the attribute. The default list of codes depends on the level of encryption that is specified by the ENCRYPTION system initialization parameter.
When you use the CEDA transaction to define the resource, CICS automatically initializes the attribute with a default list of acceptable codes. For CICS to initialize the attribute, the KEYRING system initialization parameter must be specified in the CICS region where you are running CEDA. If KEYRING is not set, CICS does not initialize the attribute. The default list of codes depends on the level of encryption that is specified by the ENCRYPTION system initialization parameter.- For ENCRYPTION=STRONG, the default value is 35363738392F303132330A1613100D15120F0C.
 For ENCRYPTION=ALL, the default value is
35363738392F303132330A1613100D15120F0C.
For ENCRYPTION=ALL, the default value is
35363738392F303132330A1613100D15120F0C.
 For ENCRYPTION=TLS12FIPS, the default
value is 35363738392F303132330A1613100D.
For ENCRYPTION=TLS12FIPS, the default
value is 35363738392F303132330A1613100D.
You can reorder the cipher codes or remove them from the initial list. However, you cannot add cipher codes that are not in the default list for the specified encryption level. To reset the value to the default list of codes, delete all of the cipher suite codes. The field is automatically repopulated with the default list.
For more information, see Cipher suites.
- DESCRIPTION(text)
- You can provide a description of the resource that you are defining in this field. The description text can be up to 58 characters in length. No restrictions apply to the characters that you can use. However, if you use parentheses, ensure that for each left parenthesis there is a matching right one. If you use the CREATE command, for each single apostrophe in the text, code two apostrophes.
- DNSGROUP(dnsgroup)
- Specifies the group name with which CICS registers
to Workload Manager, for connection optimization. The value can be
up to 18 characters, and any trailing blanks are ignored. This parameter
is referred to as group_name by the TCP/IP DNS documentation and is
the name of a cluster of equivalent server applications in a sysplex.
It is also the name within the sysplex domain that clients use to
access the CICS TCPIPSERVICE.
More than one TCPIPSERVICE might specify the same group name. The register call is made to WLM when the first service with a specified group name is opened. Subsequent services with the same group name do not cause more register calls to be made. The deregister action is dictated by the GRPCRITICAL attribute. It is also possible to explicitly deregister CICS from a group by issuing a master terminal or SPI command.
- GROUP(groupname)
- Every resource definition must have a GROUP name. The resource
definition becomes a member of the group and is installed in the CICS
system when the group is installed.
Acceptable characters:
Any lowercase characters that you enter are converted to uppercase.A-Z 0-9 $ @ #The GROUP name can be up to 8 characters in length. Lowercase characters are treated as uppercase characters. Do not use group names beginning with DFH, because these characters are reserved for use by CICS.
- GRPCRITICAL({NO|YES})
- Marks the service as a critical member of the DNS group, meaning that this service closing or failing causes a deregister call to be made to WLM for this group name. The default is NO, allowing two or more services in the same group to fail independently while CICS remains registered to the group. Only when the last service in a group is closed is the deregister call made to WLM, if it has not already been done so explicitly. Multiple services with the same group name can have different GRPCRITICAL settings. The services that specify GRPCRITICAL(NO) can be closed or fail without causing a deregister. If a service with GRPCRITICAL(YES) is closed or fails, the group is deregistered from WLM.
- HOST({ANY|DEFAULT|hostname})
- Specifies the 116-character IPv4 or IPv6 address or host name
on which CICS listens for incoming
connections. Use HOST instead of IPADDRESS when you define new resources.
Do not specify both HOST and IPADDRESS because HOST always takes
precedence over IPADDRESS. IPADDRESS is supported for existing programs
that specify IPv4 function.Possible values are as follows:
- ANY
- The ANY option has the same function as the ANY and INADDR_ANY options of IPADDRESS. The ANY option specifies that CICS listens on any of the addresses that are known to TCP/IP for the host system. You can define multiple IP addresses for a host. By specifying ANY, you also allow for the TCPIPSERVICE definition to be shared among CICS servers. If you specify ANY, CICS attempts to bind to the port on every stack where it is defined. If, in addition, you want more than one CICS region to bind to the port, you must specify the SHAREPORT option in every stack where the port is defined. If you do not do so, only one CICS region can bind to the port number in those stacks that do not have the SHAREPORT option. Subsequent attempts by other regions to bind to every stack fail, and CICS issues a message to indicate that the port is in use.
- If you specify the ANY option in a dual-mode (IPv4 and IPv6) environment, CICS attempts to reuse the most recent IPv4 or IPv6 address. If this is the first connection, and CICS cannot retrieve an address, 0.0.0.0 is returned, and no affinity is assigned.
- DEFAULT
- The DEFAULT option assigns affinity to the TCP/IP stack that is defined as the default in a multistack CINET environment.
- If the DEFAULT option is used in a dual-mode (IPv4 and IPv6) environment, affinity is assigned to the IPv4 environment because the DEFAULT option is applied to the IPv4 environment.
- If DEFAULT is used in a non-CINET environment or no default TCP/IP stack exists, an exception trace is written, 0.0.0.0 is returned, and no affinity is assigned.
- If you are operating in a dual-mode (IPv4 and IPv6) environment, specifying HOST(DEFAULT) forces all traffic to pass across the IPv4 network connection.
- hostname
- hostname can be a character host name, an IPv4
address, or an IPv6 address.
You can specify an address as a character name that can be looked up on the domain name server. The host name can be entered in uppercase, lowercase, or mixed case, but if a host name is specified instead of an IP address, the host name is converted to lowercase in the TCPIPSERVICE definition.
Do not use a character host name if you have a list of addresses at the domain name server, because hostname resolves against the first IP address only in the list (that is, the server does not listen on any of the IP addresses in the list for this host name). If you require a particular IP address in a list at the domain name server, define the IP address explicitly in hostname.
If you specify an IPv6 address (or a host name that resolves to an IPv6 address), ensure that you are operating in a dual-mode (IPv4 and IPv6) environment and that the client or server that you are communicating with is also operating in a dual-mode (IPv4 and IPv6) environment. For more information about IPv6, see Understanding IPv6 and CICS.
You can specify IPv4 and IPv6 addresses in a number of acceptable formats. For more information about address formats, see IP addresses .
- IPADDRESS({ANY|INADDR_ANY|DEFAULT|ipaddress})
- Specifies the dotted decimal IPv4 address on which this TCPIPSERVICE
listens for incoming connections. It must be of the form nnn.nnn.nnn.nnn where nnn is
in the range 0 - 255. You can use the HOST attribute
to specify the same information as IPADDRESS, but HOST also supports
an IPv6 format address and character host name. If you are using IPv6
connections, you must use the HOST attribute for your definitions
instead of IPADDRESS. HOST always takes precedence over IPADDRESS.
The IPADDRESS attribute interacts with HOST in a number of ways:
- If you specify HOST, IPADDRESS is always overwritten with a value
that depends on the contents of HOST:
- If you specify an IPv4 address, ANY, or DEFAULT in HOST, IPADDRESS is overwritten with the contents of HOST.
- If you specify an IPv6 address or a character host name in HOST, IPADDRESS is overwritten with blanks.
- If you specify both HOST and IPADDRESS, the HOST value is always
used:
- If HOST contains an IPv4 address, ANY, or DEFAULT, IPADDRESS is populated with the contents of HOST.
- If HOST contains an IPv6 address, IPADDRESS is overwritten with blanks.
If you specify an IP address of 0.0.0.0 and the HOST option is blank, a warning is issued and the value ANY is assumed.
IPADDRESS is supported for existing IPv4 function only. Use the HOST option for new resources. - If you specify HOST, IPADDRESS is always overwritten with a value
that depends on the contents of HOST:
- Possible values are as follows:
- ANY or INADDR_ANY
- The TCPIPSERVICE listens on any of the addresses that are known
to TCP/IP for the host system. It is possible to have multiple IP
addresses defined for a host. Specifying ANY or INADDR_ANY also allows
for the TCPIPSERVICE definition to be shared among CICS servers.
If you specify ANY or INADDR_ANY, CICS attempts to bind to the port on every stack where it is defined. If, in addition, you want more than one CICS region to bind to the port you must specify the SHAREPORT option in every stack where the port is defined. If you do not do so, only one CICS region is able to bind to the port number in those stacks that do not have the SHAREPORT option. Subsequent attempts by other regions to bind to every stack fails: CICS issues a message to indicate that the port is in use. For information about the SHAREPORT option, see z/OS Communications Server: IP Configuration Reference.
- DEFAULT
- Assigns affinity to the TCP/IP stack that is defined as the default in a multi-stack CINET environment. If DEFAULT is used in a non-CINET environment or there is no default TCP/IP stack, then an exception trace is written and no affinity is assigned.
- ipaddress
- The TCPIPSERVICE accepts connections on this particular address. If the address specified is not known to TCP/IP on the host system, the TCPIPSERVICE does not open. If you enter a specific address here, this definition might not be valid for CICS servers that are running on other regions, and you might not be able to share the definition with those servers.
- MAXDATALEN({32|number})
- Specifies, in kilobytes, the maximum length of data that can be received by CICS as an HTTP server, on the HTTP protocol or the USER protocol. The default value is 32 KB. The minimum is 32 KB, and the maximum is 524,288 KB. To increase security for CICS web support, specify this option on every TCPIPSERVICE definition for the HTTP protocol. It helps to guard against denial of service attacks that involve the transmission of large amounts of data.
- MAXPERSIST({NO|number})
- Specifies the maximum number of persistent connections from web
clients that the CICS region
allows for this port at any one time. This setting applies only for
the HTTP protocol.
- The default value NO means that there is no limit on the number of persistent connections.
- In a CICS region that is at risk of being overloaded with persistent connections, you can specify a suitable value (up to a theoretical maximum of 65535) based on the number of persistent connections that the CICS region can handle simultaneously. When this limit is reached and further web clients connect on the port, CICS requires the new clients to close the connection after they receive each response. When the new clients reconnect, if they connect to another CICS region that shares the port and has not reached its limit, they can maintain a persistent connection there instead. An HTTP/1.1 server normally allows persistent connections, so set this option only in a CICS region that has experienced performance problems due to persistent connections from long-lived web clients.
- If you specify a value of zero for this option, the CICS region does not allow persistent connections and requires every web client to close the connection after they receive each response. A zero setting for MAXPERSIST is not compliant with the HTTP/1.1 specification, so use that setting only if you have a special requirement for it in a CICS region that is not currently handling external requests, for example, in a test environment.
- PORTNUMBER(port)
- Specifies, in the range 1 - 65535, the decimal number of the port
on which CICS is to listen
for incoming client requests. The well-known ports are those from 1 through 1023. It is advisable to use well-known port numbers only for those services to which they are normally assigned. The well-known ports for services that are supported by CICS are as follows:
- 80
- HTTP (non-SSL)
- 443
- HTTP with SSL
- 1435
- ECI (Registered port number)
Take care to resolve conflicts with any other servers on the same MVS™ image that might use the well-known ports.
Port sharing must be enabled for any port that you want to share across CICS systems within an MVS image. For more information, see z/OS Communications Server: IP Configuration Reference.
- PRIVACY
- This attribute is obsolete, but is supported to provide compatibility with earlier releases of CICS. For more information, see Obsolete attributes.
- PROTOCOL({HTTP|IIOP|ECI|IPIC|USER})
- Specifies the application level protocol that is used on the TCP/IP
port.
- HTTP
- HTTP protocol is used. HTTP protocol is handled by CICS Web support. CICS performs basic acceptance checks for messages that are sent and received using this protocol. This protocol is required for the well-known ports 80 (used for HTTP without SSL) and 443 (used for HTTP with SSL).
- IIOP
- The IIOP attribute in TCPIPSERVICE definitions is obsolete but is retained for compatibility reasons.
- ECI
- The CICS ECI protocol is used.
- IPIC
- IPIC protocol is used. Specify IPIC for TCPIPSERVICE resources that are to be used for distributed program link (DPL) over IP interconnectivity connections (which are also known as IPCONNs).
- USER
- The user-defined protocol is used. Messages are processed as non-HTTP messages. They are flagged as non-HTTP and passed unchanged to the analyzer program for the TCPIPSERVICE resource. CICS Web support facilities are used for handling the request, but no acceptance checks are carried out for messages that are sent and received by using this protocol. Processing for all non-HTTP requests must be carried out under the USER protocolso that they are protected from the basic acceptance checks that CICS carries out for requests by using the HTTP protocol. If an HTTP message is handled by the USER protocol, you are responsible for checking its validity.
- REALM(string)
- Specifies the realm that is used for HTTP basic authentication.
You can specify this attribute only for the HTTP protocol.
The realm is provided by CICS in the WWW-Authenticate header, and is seen by the user during the process of basic authentication. It identifies the set of resources to which the authentication information requested (that is, the user ID, and password or password phrase) applies.
If you do not specify a realm, the default that is used by CICS is CICS application aaaaaaaa, where aaaaaaaa is the APPLID of the CICS region.
The realm can be up to 56 characters, and can include embedded blanks. It is specified in mixed case, and the case is preserved. Do not specify opening and closing double quotation marks, as CICS provides these when it assembles the WWW-Authenticate header.
Acceptable characters:
Space characters are also permitted. If parentheses are used, you must use them as pairs of opening and closing parentheses.A-Z a-z 0-9 $ @ # . - _ % & ? ! : | ' = ¬ + * , ; < > ( ) - SOCKETCLOSE({NO|hhmmss})
- Specifies whether, and for how long, CICS waits before it closes the socket. The SOCKETCLOSE attribute does not apply to the first receive request that is issued after a connection is made. On the first receive request for the ECI and USER protocols, CICS waits for data for 30 seconds before it closes the socket. On the first receive request for the HTTP protocol, CICS waits for the DTIMEOUT value associated with the transaction specified on the TCPIPSERVICE. If this DTIMEOUT value is zero CICS waits for 30 seconds.
The interval is measured from the time of the initial receive request for incoming data on that socket.
- NO
- The socket is left open until it is closed by the client, or by a user application program in CICS.
- hhmmss
- The interval (in HHMMSS format) from the time of the initial receive request for incoming data, after which CICS is to timeout the socket. Choose a value that is appropriate to the responsiveness of the client, and the reliability of your network. Specifying 000000 closes the socket immediately if no data is available for any receive requests other than the first one.
If you are using this TCPIPSERVICE resource for CICS web support with the HTTP protocol, a zero setting for SOCKETCLOSE means that CICS closes the connection immediately after it receives data from the web client, unless further data is waiting. This setting means that persistent connections cannot be maintained, and it is not compliant with the HTTP/1.1 specification. Use a zero setting for SOCKETCLOSE with the HTTP protocol only if you have a special requirement for it in a CICS region that is not currently handling external requests, for example, in a test environment.
If you specify PROTOCOL(ECI) or PROTOCOL(IPIC), you must specify SOCKETCLOSE(NO).
If you specify PROTOCOL(USER), persistent sessions are not supported, and you must specify SOCKETCLOSE(000000).
After the TCPIPSERVICE resource is installed, you cannot change this value by using CEMT; you must set the TCPIPSERVICE resource out of service, then reinstall the TCPIPSERVICE resource with the modified definition.
- SSL({NO|YES|CLIENTAUTH})
- Specifies whether the TCP/IP service is to use the secure sockets
layer (SSL) for encryption and authentication. You can specify
this attribute for the HTTP, USER, and IPIC protocols, but not for
the ECI protocol. Note:
 When they use SSL, MAXSSLTCBs
should be set to a value that is at least twice the number of IPIC
connections that use SSL by the CICS region.
When they use SSL, MAXSSLTCBs
should be set to a value that is at least twice the number of IPIC
connections that use SSL by the CICS region.
- NO
- SSL is not to be used. No security checks are applied when the connection is being acquired. No encryption is applied to outbound messages.
- YES
- An SSL session is to be used; CICS sends a server certificate to the client. SSL decryption processing is applied to all messages that arrive at this port. The level of encryption that is applied to inbound messages is found from the value of the CIPHERS attribute.
- CLIENTAUTH
- An SSL session is to be used; CICS sends a server certificate to the client. CICS expects to receive a client certificate from the partner system during the SSL handshake, when the connection is being acquired.
- STATUS({OPEN|CLOSED})
- Indicates the initial status of the service after installation. Set it to OPEN if CICS is to begin listening for this service after installation. Set to CLOSE if CICS is not to listen on behalf of this service after installation.
- TCPIPSERVICE(name)
- Specifies the 8-character name of this service.
Acceptable characters:
Unless you are using the CREATE command, any lowercase characters that you enter are converted to uppercase.A-Z 0-9 $ @ # - TRANSACTION(transaction)
- Specifies the 4-character ID of the CICS transaction
that is attached to process new requests that are received for this
service.
- For an ECI over TCP/IP TCPIPSERVICE resource, specify CIEP (or another transaction that executes program DFHIEP).
- For an HTTP TCPIPSERVICE resource, specify CWXN (or another transaction that executes program DFHWBXN).
- For an IPIC TCPIPSERVICE resource, specify CISS (or another transaction that executes program DFHISCOP).
- For a USER TCPIPSERVICE resource, specify CWXU (or another transaction that executes program DFHWBXN).
- TSQPREFIX(prefix)
- This attribute is obsolete, but is supported to provide compatibility with earlier releases of CICS. For more information, see Obsolete attributes.
- URM({NO|program_name})
- Specifies the name of a user-replaceable program to be started
by this service.
- NO
- Autoinstall is not permitted with this TCPIPSERVICE resource. This is only applicable for PROTOCOL(IPIC).
- program_name
- For those protocols for which URM is a required attribute, the
default program name depends upon the value of the PROTOCOL attribute:
- For the HTTP protocol, specify the name of an analyzer program to be associated with this TCPIPSERVICE resource. The CICS-supplied analyzer program DFHWBAAX is the default. DFHWBAAX provides basic error handling when all requests on the port should be handled by URIMAP definitions (for example, web service requests). It does not provide support for requests that use the URL format that CICS web support used before CICS TS 3.1. If you must provide support for requests that are not handled by URIMAP definitions, the analyzer program that is specified for your TCPIPSERVICE resource must be the CICS-supplied sample analyzer program DFHWBADX or your own customized analyzer program. For more information about analyzer programs, see Analyzer programs.
- For the IPIC protocol, specify the name of the autoinstall user program for IPCONNs, if required. For PROTOCOL(IPIC), if you do not specify this attribute CICS uses the CICS-supplied default autoinstall user program, DFHISAIP.
- For the USER protocol, specify the name of an analyzer program to be associated with this TCPIPSERVICE definition. The analyzer program must be present, and it handles all requests on this protocol. The CICS-supplied sample analyzer program, DFHWBADX, is suitable. For more information about analyzer programs, see the Analyzer programs.