Troubleshooting
Problem
The default configuration for Single Sign-On for the i5 is to add user accounts on active directory. This can result in many accounts, each with a password assigned and therefore adding to administration of these accounts by Windows administrators. This document includes a method on how to have multiple service principals attached to one account with no password assigned to it.
Resolving The Problem
The default configuration for Single Sign-On for the i5 is to add user accounts on active directory. This can result in many accounts, each with a password assigned and therefore adding to administration of these accounts by Windows administrators. This document includes a method on how to have multiple service principals attached to one account with no password assigned to it.
Important Note: This document relies heavily on the use of the command KTPASS. There is a known bug where certain versions of the KTPASS command will incorrectly hash the salt value in the keytab file in Windows Server 2003. Prior to using this document, the version of the KTPASS command should be checked:
Right click on the ktpass.exe file usually located in the C:\Program Files\Support Tools directory, and click Properties. If the version shows 5.2.3790.1830, the support tools must be updated using the Microsoft Techdoc available at the following URL:
//www.microsoft.com/en-us/download/details.aspx?id=15326 (this link is valid as of 8/30/2012)
The newer KTPASS version does not have this issue.
One method to have multiple service principals attached to one account with no password assigned is to use a computer account instead of a user account. To add these principles, you should follow the steps below:
| 1. | After the EIM and NAS configuration have been completed, do not run the batch file that was created on the Active directory server; instead, rename the krb5.keytab file located in the following: /QIBM/UserData/OS400/NetworkAuthentication/keytab/ This will be replaced on the last step. | ||||||||||||||||||||||||
| 2. | On the active directory server, create a computer account with the name of the System i and run the command ktpass as follows: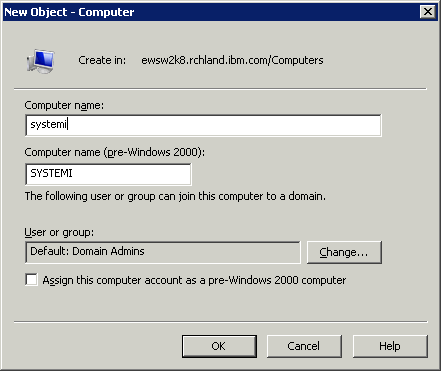 ktpass -out c:\krb5.keytab -princ krbsvr400/systemi.mycompany.com@MYCOMPANY.COM -pass password -mapuser systemi$@mycompany.com -mapop set +answer +DesOnly -crypto DES-CBC-MD5 -ptype KRB5_NT_SRV_HST /kvno 2 -setupn Notes: 1. Each additional service principal can be added like the examples below. Notice the -in parameter has been added. For additional assistance with the ktpass command, you should contact Microsoft support. The -mappuser option should be the computer account added in Step 1, and it needs the $ before the @ sign. Examples ktpass -in c:\krb5.keytab -out c:\krb5.keytab -princ HOST/systemi.mycompany.com@MYCOMPANY.COM -pass password -mapuser systemi$@mycompany.com -mapop add +answer +DesOnly -crypto DES-CBC-MD5 -ptype KRB5_NT_SRV_HST /kvno 2 -setupn ktpass -in c:\krb5.keytab -out c:\krb5.keytab -princ cifs/systemi.mycompany.com@MYCOMPANY.COM -pass password -mapuser systemi$@mycompany.com -mapop add +answer +DesOnly -crypto DES-CBC-MD5 -ptype KRB5_NT_SRV_HST /kvno 2 -setupn 2. The above examples use the DES encryption type which is obsolete, and many security policies may prohibit the use. In order to use the AES/RC4 encryption, the following PTFs need to be applied and the ktpass would need to be modified as follows:
ktpass -out c:\krb5.keytab -princ krbsvr400/systemi.mycompany.com@MYCOMPANY.COM -pass password -mapuser systemi$@mycompany.com -mapop set +answer -crypto RC4-HMAC-NT -ptype KRB5_NT_SRV_HST /kvno 2 -setupn | ||||||||||||||||||||||||
| 3. | Once all the principals have been added, you should FTP the c:\krb5.keytab file in binary to the i5 located in the following: /QIBM/UserData/OS400/NetworkAuthentication/keytab/ | ||||||||||||||||||||||||
| 4. | Connect with a session using Kerberos. Note: kinit -k will not work for testing because this is a computer account. If the connection fails, you should contact IBM Support. |
Historical Number
636975959
Was this topic helpful?
Document Information
Modified date:
18 December 2019
UID
nas8N1010920