How To
Summary
In many network environments, there are multiple AD servers used. The NAS configuration wizard on IBM i only allows for a single AD server to be added. This document describes how to manually add one or more additional AD servers to the configuration.
Objective
Add a second KDC to the Single Signon environment.
Steps
The steps in this document are intended to be performed once a working Kerberos Single Signon (SSO) environment has been set on the IBM i. The setup steps used assume a Microsoft Windows Active Directory is used, however this can be utilized with other platforms acting as a Kerberos KDC (Key Distribution Center). As this is a manual configuration/edit/change which must be performed on the IBM i and the KDC used, these steps are provided as-is and are not intended to be used as an HA (High Availability) solution. If an HA solution is needed, IBM's Lab Services can be contacted to discuss terms.
Edit the Network Authentication Service (NAS) configuration file to add the new KDC
- On an IBM i command line, copy/paste the following and hit Enter:
EDTF '/QIBM/UserData/OS400/NetworkAuthentication/krb5.conf'
- You should see your network domain and possibly two indented lines under it for kdc and kpasswd_server (kpasswd_server was an option during the configuration of NAS so it may not be listed depending on your selections)
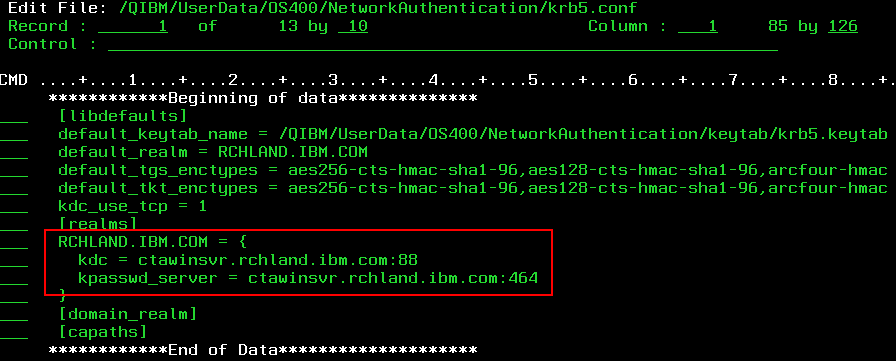
- Put the letter "i" in the line next to the kpasswd_server and hit Enter to insert a blank line (or next to the kdc if you don't have kpasswd_server). *Note* To delete a line, put the letter "D" next to the line you wish to delete.
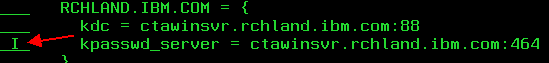
- Copy the kdc = <servername> that is already there, then use the same indent spacing and paste it into the blank line. Change the system name to match what your additional KDC name should be (AD server name). If you also need to add the kpasswd_server line for the new system, use the same instruction (copy/paste the line and change the name).
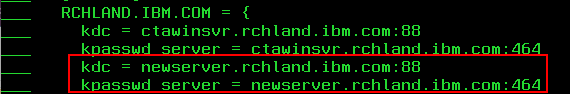
- F3 to Save/Exit the file.
The steps above will allow the system to receive Kerberos tickets issued by the secondary KDC (AD server). It is up to the customer to replicate/migrate the Active Directory (or whatever type of server is used) entries to the secondary KDC. If a batch file was run on the original AD server, the same batch file may be used on the secondary server to add the same entries.
*NOTE*
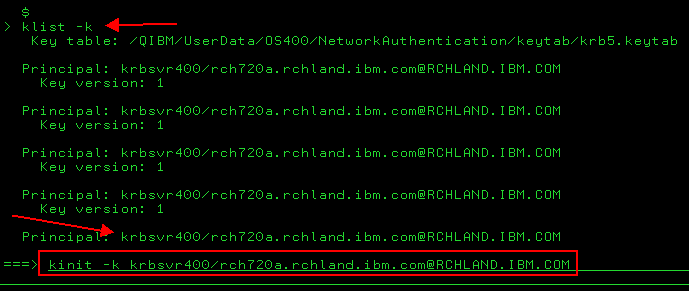
Once the AD entries are replicated on the secondary system, you can use the kinit -k <service principal name> from QSHELL to test, however you should edit the configuration file and cut the original KDC server out and save the file first. This ensures you are not going to the original server for the test. If the kinit -k command is successful you will get a $ prompt (see images below). Once testing is complete, re-add the original KDC into the krb5.conf file.
Once the AD entries are replicated on the secondary system, you can use the kinit -k <service principal name> from QSHELL to test, however you should edit the configuration file and cut the original KDC server out and save the file first. This ensures you are not going to the original server for the test. If the kinit -k command is successful you will get a $ prompt (see images below). Once testing is complete, re-add the original KDC into the krb5.conf file.
Additional Information
Terminology used in this document:
KDC: Key Distribution Center. This is the server that users authenticate to on the network and is responsible for generating Kerberos tickets which will be used to authenticate to the IBM i without signing in.
AD server: Active Directory server. This is Microsoft's proprietary implementation of LDAP with other services included and runs on a Windows Server. User profiles and other data are entered here to allow them to authenticate to the network in a Windows network environment.
Related Information
Document Location
Worldwide
[{"Type":"MASTER","Line of Business":{"code":"LOB57","label":"Power"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"SWG60","label":"IBM i"},"Platform":[{"code":"PF012","label":"IBM i"}],"Version":"7.2.0"}]
Was this topic helpful?
Document Information
Modified date:
26 June 2019
UID
ibm10957333