If authentication and mapping are configured, they are used to verify the identity before it is authorized.
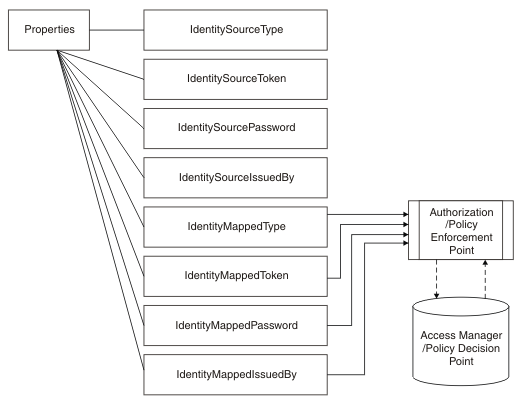
If a mapped identity exists, authorization is applied to the mapped identity. If a mapped identity does not exist, the source identity is used.
If you specify LDAP as the provider for authorization, the security manager queries the configured LDAP server (which must be LDAP Version 3 compliant), to validate that the identity is a member of the LDAP group that is configured in the security profile.
If you specify WS-Trust v1.3 STS as the provider for authorization, the security manager invokes the security token server (STS), such as Tivoli® Federated Identity Manager (TFIM) V6.2, to validate that the identity token provided has permission to access the message flow. If you are using TFIM V6.1 rather than TFIM V6.2, you can specify TFIM as the provider for authorization.
For more information about using TFIM V6.2 for authorization, see Authentication, mapping, and authorization with TFIM V6.2 and TAM.
For information about using TFIM V6.1 for authorization, see Authentication, mapping, and authorization with TFIM V6.1 and TAM.
 Last updated Friday, 21 July 2017
Last updated Friday, 21 July 2017