Use the following directions to run IKYSETUP only if you have not
done so for a previous release (or if you are changing values).
You can use the following directions to run IKYSETUP with minimal
changes or to extensively customize it.
Guideline: If this is your first attempt to use IKYSETUP,
change only the IKYSETUP variables in the section Things you
must change. You can refine IKYSETUP later, after you are
familiar with the process of updating and running it.
The following flowchart illustrates the iterative nature of the
process of updating IKYSETUP:
Figure 1. Flowchart
of the process of updating IKYSETUP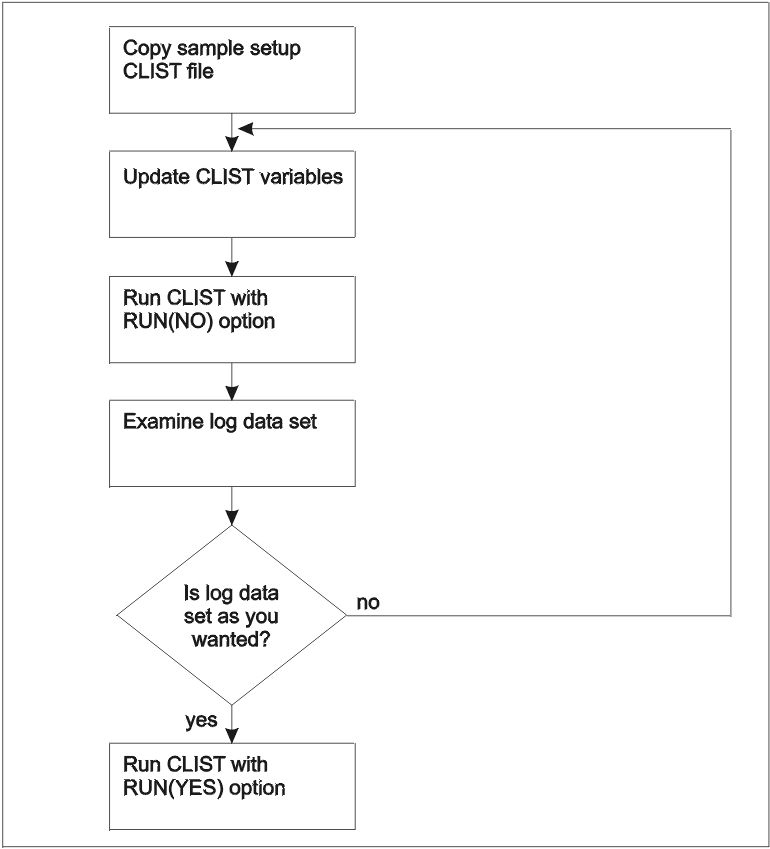
Perform the following steps to use IKYSETUP to perform RACF® administration tasks:
- Copy SYS1.SAMPLIB(IKYSETUP) to a data set you
are permitted to edit.
_______________________________________________________________
- Edit
the IKYSETUP code to update the values of variables you changed in Table 1.
The
following example shows how to change the pkigroup_mem. variables.
(Remember that for pkigroup_mem., you set pkigroup_mem.0 to
the number of items in the list and pkigroup_mem.1 through pkigroup_mem.n to
the PKI Services administration
group member IDs.)
Example:pkigroup_mem.0=3 /* Number of pkigroup members to connect */
pkigroup_mem.1="TOM"
pkigroup_mem.2="DICK"
pkigroup_mem.3="HARRY"
_______________________________________________________________
- If necessary, update the values of variables you changed
in Table 1.
The
following example shows how to change the key_type variable.
_______________________________________________________________
- Optionally update any variables you changed in Table 1.
The
following example shows how to change the log_dsn variable.
_______________________________________________________________
- Run IKYSETUP by entering the following command:
EX 'data-set-name(IKYSETUP)' 'RUN(NO)'
Note: - The user ID that runs IKYSETUP must be a RACF SPECIAL user ID.
- When IKYSETUP runs, it prompts you to enter your secret passphrase.
(This is for encrypting the backup copy of your CA certificate and
private key.) Be aware that asterisks do not replace the secret passphrase;
it appears on the screen in the clear.
Important: Make a
note of this passphrase. If you forget it, your backup will be useless.
- The NO option in the command specifies displaying the commands
only. (This creates a log data set listing the commands and other
information. Alternative parameters are: YES, which indicates running
IKYSETUP as is, and PROMPT, indicates prompting the user before running
each command.)
_______________________________________________________________
- Review the log data set. (See Sample IKYSETUP log data set for
an example of the data that appears on your display when you are running
IKYSETUP; this is similar to the contents of the log data set.) The
top part identifies the tasks and shows the commands that run to perform
those tasks. Review this to ensure that the issued commands match
your expectations. (For more information about these commands, see Actions IKYSETUP performs by issuing RACF commands.) The bottom part provides a record of
important information that you will need for later steps, such the
name of your daemon user ID. Review this information to ensure that
the values are the ones you want.
If you want to change any of the
commands or information in the log data set, you need to change additional
values in IKYSETUP. Remember to record any additional changes in Table 1, Table 1,
and Table 1.
Then go back to Step 3.
_______________________________________________________________
- If the log data set includes the commands and information you
want, rerun the IKYSETUP code by entering the following command:
EX 'data-set-name(IKYSETUP)' 'RUN(YES)'
_______________________________________________________________
- After running IKYSETUP with RUN(YES), examine
the results recorded in the log data set. Investigate and rerun (potentially
by hand) any failing commands. Investigate informational messages
and make any necessary corrections. (Informational messages usually
indicate a setup problem that might affect operations later. For example,
any informational message from the RACDCERT commands that indicate
that the certificate has been marked NO TRUST is
an error.)
_______________________________________________________________
- If you intend to use encrypted LDAP passwords, you need to perform
additional RACF administration
tasks; see Using encrypted passwords for LDAP servers.
_______________________________________________________________
 z/OS Cryptographic Services PKI Services Guide and Reference
z/OS Cryptographic Services PKI Services Guide and Reference
 z/OS Cryptographic Services PKI Services Guide and Reference
z/OS Cryptographic Services PKI Services Guide and Reference




 Copyright IBM Corporation 1990, 2014
Copyright IBM Corporation 1990, 2014