 z/OS Security Server RACF System Programmer's Guide
z/OS Security Server RACF System Programmer's Guide
 z/OS Security Server RACF System Programmer's Guide
z/OS Security Server RACF System Programmer's Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
RACF and the operating system z/OS Security Server RACF System Programmer's Guide SA23-2287-00 |
|
|
RACF® acts as a layer in the operating system. For example:
Figure 1 shows how RACF interacts with the operating system to allow access to a protected resource. The operating system-RACF interaction to identify and verify users is similar. Figure 1. RACF and its relationship to the operating system
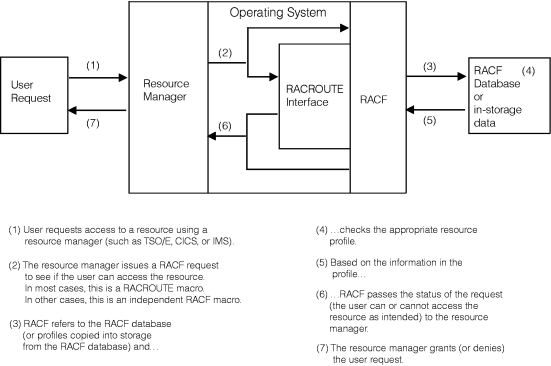 During authorization checking, RACF ensures that a user has the authorization to access the requested protected resource. RACF checks the resource profile to ensure, for example, that the resource can be accessed in the way requested and that the user has the proper authorization to access the resource. The RACF mechanism is analogous to the tumblers of a lock, all of which must align before the lock can open. In RACF, the necessary user-resource requirements must match before RACF grants the request to access a protected resource. 


|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |