 z/OS JES2 Initialization and Tuning Guide
z/OS JES2 Initialization and Tuning Guide
 z/OS JES2 Initialization and Tuning Guide
z/OS JES2 Initialization and Tuning Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
DUPLEX (with backup) on Coupling facility z/OS JES2 Initialization and Tuning Guide SA32-0991-00 |
|
|
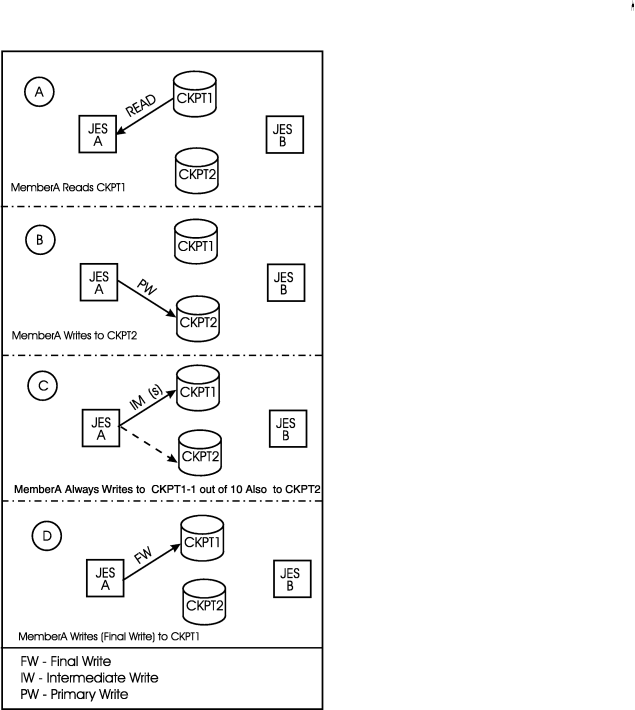
If you define both checkpoint data sets on different structures within different Coupling facilities, performance should be increased significantly. The primary data set is specified by the CKPT1= parameter on the CKPTDEF initialization statement and the duplex data set is specified by the CKPT2= parameter on that same statement: The CKPT1 data set is the primary data set, that is, it is read from and written to at every intermediate read and final write of the checkpoint by all members in your multi-access spool configuration. The duplex data set, CKPT2, is updated less frequently (that is, once for every 10 writes to the primary). If the primary data set suffers an error, the duplex can provide either an exact duplicate of the primary or a very similar, almost current (depending on when it was last updated) copy, of the checkpoint data. Figure 1 and Figure 2 provide diagrammatic views of this processing. See these
figures as you read the following example of duplex processing. Assume
a 2-member multi-access spool configuration: members JESA and JESB,
the primary checkpoint named CKPT1 and duplex named CKPT2.
Figure 1. Checkpoint data set processing, DUPLEX mode, two-member multi-access
spool configuration - JESA cycle
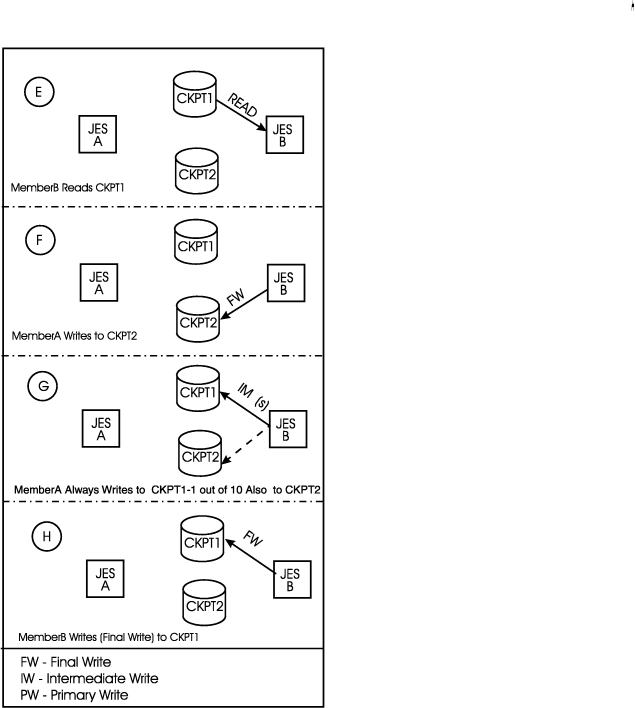
 JESB now gains checkpoint control (Figure 2);
Figure 2. Checkpoint data set processing, DUPLEX mode, two-member multi-access
spool configuration - JESB cycle
 Even if the primary checkpoint data set, CKPT1, is updated every checkpoint cycle, and the duplex, CKPT2, is updated on a regular basis, when an error occurs on the primary checkpoint data set, a more current copy of the checkpoint might be available to the member that experienced the error. Each member holds an “in-storage” copy of the checkpoint, which it uses to update the checkpoint. This in-storage data set can be copied into the “replacement checkpoint”, NEWCKPTn, data set if one has been predefined (by initialization statement), or dynamically added (by operator command), or in response to checkpoint reconfiguration dialog messages. However, if the member holding this up-to-date in-storage copy has also suffered a failure, the most up-to-date copy of the checkpoint available would be defined by the duplex checkpoint data set. Attention: DUPLEX mode checkpoint processing is recommended for single
member configurations and required if any checkpoint data set resides
on a Coupling facility structure.


|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |