Integrating IBM WebSphere DataPower with a cluster of instances of MobileFirst Server
You can use IBM® WebSphere® DataPower® as a gateway for all incoming connections for IBM MobileFirst™ Platform Foundation and Application Center, and IBM HTTP Server (IHS) for load-balancing MobileFirst Server that are deployed on an IBM WebSphere Application Server 8.5 cluster or a Liberty profile server farm.
Before you begin
Ensure that the following environments are available:
- MobileFirst Server is deployed on an IBM WebSphere Application Server ND cluster or on a Liberty profile server farm and is configured to use DB2® or any compatible database. For more information, see Typical topologies of a MobileFirst instance in an extranet infrastructure.
- IBM MobileFirst Platform Foundation Application Center is set up on an IBM WebSphere Application Server ND cluster. For more information, see Installing and configuring the Application Center.
- IBM WebSphere DataPower XI52.
- IBM HTTP Server.
- Any LDAP server with SSL enabled.
About this task
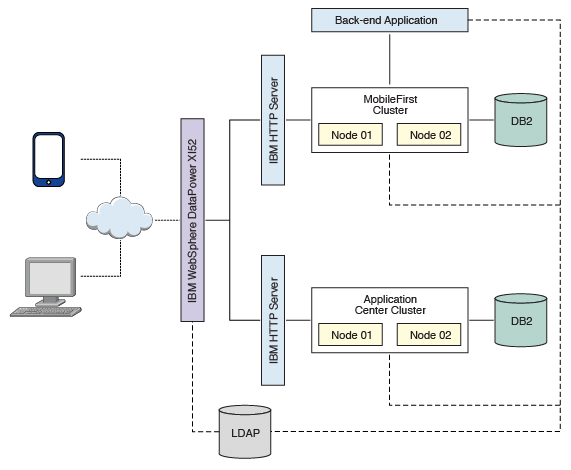
DataPower XI52 acts as the gateway for all IBM MobileFirst Platform Foundation and Application Center requests. DataPower validates all incoming user credentials against an LDAP registry. If the validation is successful, DataPower generates an LTPA token, which is present as part of a session cookie. This cookie is only valid for one session and is used for all further requests during that session. The cookies themselves contain information about the user that has been authenticated, the realm for which the user was authenticated (such as an LDAP server) and a timestamp. A request with a valid LTPA cookie can access a server that is a member of the same authentication domain as the first server. The request is automatically authenticated, thereby enabling single-sign-on (SSO).
All requests that reach the MobileFirst cluster or the backend application validate only the LTPA token. If the LTPA token is valid, the request is authenticated according to the rules that are set. The LTPA token guarantees that as long as the token is valid, all requests have SSO capability into all backend servers, including IBM MobileFirst Platform Foundation and Application Center.
The following sequence of events takes place when a mobile application makes a request (see Figure 2):
- The mobile application makes a request to the DataPower gateway.
- DataPower checks for an LTPA token in the incoming request.
- If a valid LTPA token is present, the request is sent to the IBM MobileFirst Platform Foundation cluster.
- If an LTPA token is not present or if the token is not valid, DataPower throws an authentication challenge. The mobile application handles the challenge and then prompts for user credentials.
- The MobileFirst cluster validates the LTPA token and sends the request to the backend application server along with the LTPA token.
- The backend application server validates the LTPA token and sends the response back to IBM MobileFirst Platform Foundation.
- IBM MobileFirst Platform Foundation forwards the request to DataPower, and DataPower forwards it to the requesting mobile application.
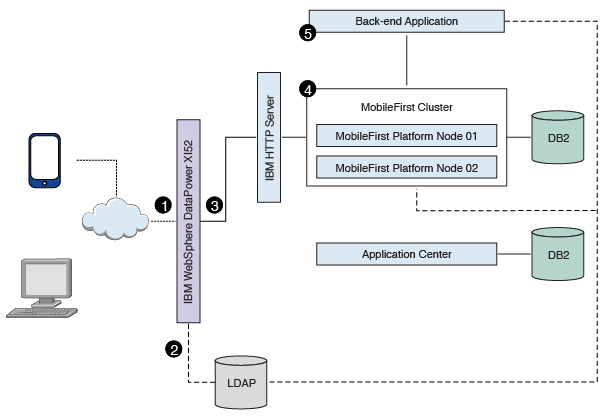
The Application Center request-response flow takes a similar route to the mobile application flow, except that requests are routed to the Application Center server instead of to the MobileFirst cluster (see Figure 3).