Summary of the certificate-related operations
Figure 1 illustrates the relationships between sending and receiving applications and relevant certificates. The scenario illustrated involves remote queuing between two z/OS® queue managers using a data-protection policy of privacy. In Figure 1, "AMS" indicates " IBM® MQ Advanced Message Security".
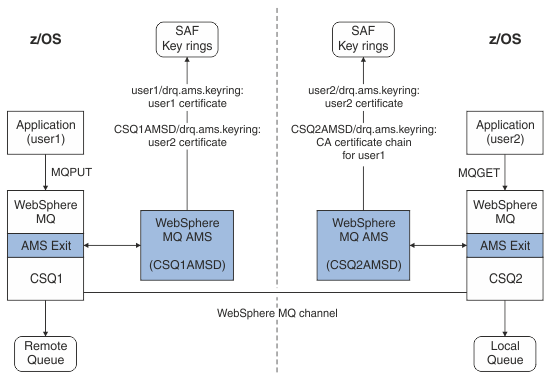
In this diagram, an application running as 'user1' puts a message to a remote queue managed by queue manager CSQ1, intended to be retrieved by an application running as 'user2' from a local queue managed by queue manager CSQ2. The diagram assumes an IBM MQ Advanced Message Security policy of privacy, which means the message is both signed and encrypted.
IBM MQ Advanced Message Security intercepts the message when a put occurs and uses user2's certificate (stored in the AMS address space user's key ring) to encrypt a symmetric key used to encrypt the message data.
Note that user2's certificate is connected to the AMS address space user key ring with option USAGE(SITE). This means the AMS address space user can access the certificate and public key, but not the private key.
On the receiving end, IBM MQ Advanced Message Security intercepts the get issued by user2, and uses user2's certificate to decrypt the symmetric key so that it can decrypt the message data. It then validates user1's signature using the CA certificate chain of user1's certificate stored in the AMS address space user's key ring.
Given this scenario, but with a data-protection policy of integrity, certificates for user2 would not be required.
To use IBM MQ Advanced Message Security to enqueue messages on IBM MQ-protected queues having a message protection policy of privacy or integrity, IBM MQ Advanced Message Security must have access to these data items:
- The X.509 V2 or V3 certificate and private key for the user enqueuing the message.
- The chain of certificates used to sign the digital certificates of all message signers.
- If the data protection policy is privacy, the X.509 V2 or V3 certificate of the intended recipients. The intended recipients are listed in the IBM MQ Advanced Message Security policy associated with the queue.
For processes and applications that run on z/OS, IBM MQ Advanced Message Security must have certificates in two places:
- In a SAF-managed key ring associated with the RACF® identity of the sending application (the application that enqueues the protected message) or receiving application (if using privacy).
The certificate that IBM MQ Advanced Message Security locates is the default certificate, and must include the private key. IBM MQ Advanced Message Security assumes the z/OS user identity of the sending application. That is, it acts as a surrogate, so it can access the user's private key.
- In a SAF-managed key ring associated with the AMS address space user.
When sending messages protected with privacy, this key ring contains the public key certificates of the message recipients. When receiving messages, it contains the chain of Certificate Authority certificates needed to validate the message sender's signature.
The earlier examples shown have used RACF as the local CA. However, you may use another PKI provider (Certificate Authority) at your installation. If you intend to use another PKI product, remember that the private key and the certificate must be imported into a key ring associated with the z/OS RACF user IDs that originate IBM MQ messages protected by IBM MQ Advanced Message Security.
You can use the RACF RACDCERT command as the mechanism to generate certificate requests, which can be exported and sent to the PKI provider of your choice to be issued.
Here is a summary of the certificate-related steps:
- Request the creation of a CA certificate, one in which RACF is the local CA. Omit this step if you are using another PKI provider.
- Generate user certificates signed by the CA.
- Create the key rings for the users and the IBM MQ Advanced Message Security AMS address space ID.
- Connect the user certificate to the user key ring with the default attribute.
- Connect the recipients certificates to the IBM MQ Advanced Message Security AMS address space user key ring using the usage(site) attribute (This step is necessary only for user certificates that will ultimately be the recipients of privacy-protected messages).
- Connect the CA certificate chains for message senders to the IBM MQ Advanced Message Security AMS address space user key ring. (This step is necessary only for AMS tasks that will be verifying sender signatures.)