IBM® Database Encryption Expert is a comprehensive software data security solution that when used in conjunction with native DB2® security provides effective protection of the data and the database application against a broad array of threats.
Database Encryption Expert is transparent to users, databases, applications, and storage. No code changes or changes to existing infrastructure are required. Database Encryption Expert can protect data in any storage environment, while users continue to access data the in the same way as before.
Database Encryption Expert can protect database applications, because it can prevent changes to executable files, configuration files, libraries, and so on, thereby preventing attacks on the application.
Database Encryption Expert is a set of agent and server software packages that you administer by using a Web-based user-interface and command-line utilities. The Database Encryption Expert administrator configures security policies that govern how security and encryption are implemented.
According to how these security policies are defined, the Database Encryption Expert backup agent encrypts DB2 backups, and the Database Encryption Expert file system agent encrypts DB2 data files.
The Encryption Expert Security Server stores the security policies, encryption keys and event log files. Security policies contain sets of security rules that must be satisfied in order to allow or deny access. Each security rule evaluates who, what, when, and how protected data is accessed and, if these criteria match, the Security Server either permits or denies access.
Figure 1 illustrates the architecture of Database Encryption Expert.
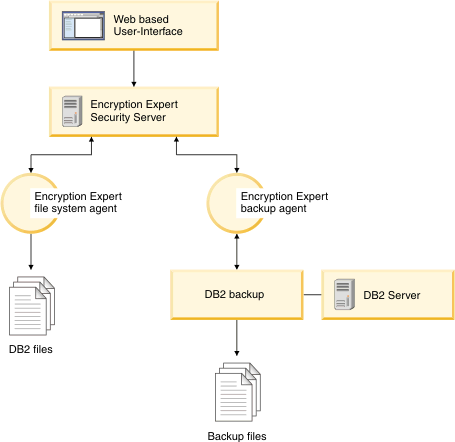
The Database Encryption Expert file system agent process is always running in the background. The agent intercepts any attempt to access data files, directories, or executables that you are protecting. The Database Encryption Expert file system agent forwards the access attempt to the Security Server and, based upon the applied policy, the Security Server grants or denies the attempted access.
Database Encryption Expert protection extends beyond simply allowing or denying access to a file, you can also encrypt files. Just the file contents is encrypted, but the file metadata is left intact. Therefore, you do not have to decrypt an encrypted file just to see it's name, timestamps, file type, and so on. This allows data management applications to perform their functions without exposing the file contents. For example, backup managers can backup specific data, without being able to see the contents.
If an encrypted file is accessed by an unauthorized user, its contents are worthless without the appropriate Security Server approval and encryption keys. However, users with the correct policies and permissions are unaware that encryption and decryption are taking place.
All database backup functions that are normally performed by the DB2 backup API system are supported by the Database Encryption Expert server, including native database compression. Other than an additional command-line argument, DB2 backup operators are unaware of Database Encryption Expert intervention. Database Encryption Expert backs up and restores static data-at-rest and active online data.
Basic backup and restore configuration is supported. In the basic configuration, data is encrypted and backed up with one server and multiple agents; data is decrypted and restored on an agent that is configured with the same server that was originally used to make the backup.
Single-site and multi-site configurations are also supported for backup and restore. In a single-site scenario, configuration data is mirrored across multiple Security Servers in a single data center. In a multi-site scenario, backups are restored on different Encryption Expert servers in different data centers.
Database Encryption Expert agent activity is closely monitored and logged through a centralized audit logging facility. All auditable events, including backups, restores, and security administration operations can be logged. This includes Database Encryption Expert system events, such as initialization, shut down and restart; and network connects and disconnects between different Database Encryption Expert components.
For more information about Database Encryption Expert, go to the following web page:http://publib.boulder.ibm.com/infocenter/mptoolic/v1r0/topic/com.ibm.db2tools.eet.doc.ug/eetwelcome.htm.