Delegations
Delegation is a process security identity propagation from a caller to a called object. As per the Java™ Platform, Enterprise Edition (Java EE) specification, a servlet and enterprise beans can propagate either the client or remote user identity when invoking enterprise beans, or they can use another specified identity as indicated in the corresponding deployment descriptor.
- Delegate (RunAs) client identity
- Delegate (RunAs) specified identity
- Delegate (RunAs) system identity
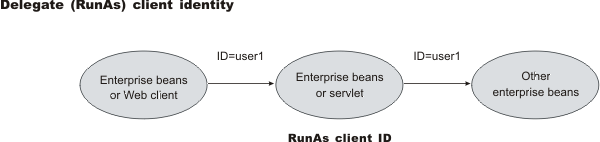
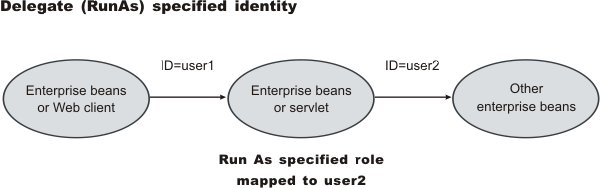
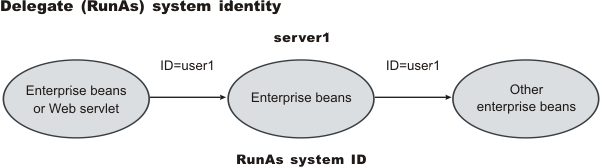
The EJB specification only supports delegation (RunAs) at the Enterprise JavaBeans (EJB) level. But an extension allows EJB method-level RunAs specification. With an EJB method level, the RunAs specification can specify a different RunAs role for different methods within the same enterprise beans.
The RunAs specification is detailed in the deployment descriptor, which is the ejb-jar.xml file in the EJB module and the web.xml file in the web module. The extension to the RunAs specification is included in the ibm-ejb-jar-ext.xml file.
An IBM-specific binding file is available for each application that contains a mapping from the RunAs role to the user. This file is specified in the ibm-application-bnd.xml file.
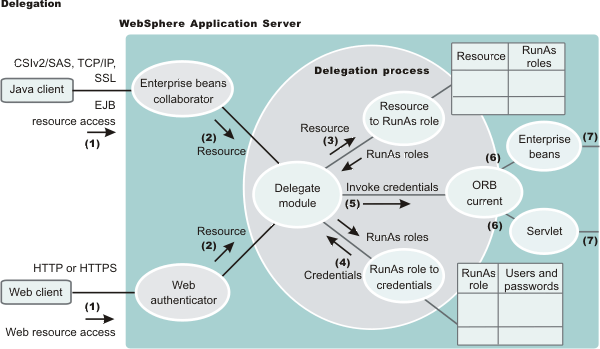
Delegation Process
- Resource to RunAs role mapping table
- RunAs role to user ID and password mapping table
Use the Resource to RunAs role mapping table to get the role that is used by a servlet or by enterprise beans to propagate to the next enterprise beans call.
Use the RunAsRole to user ID and password mapping table to get the user ID that belongs to the RunAs role and its password.
Delegation is performed after successful authentication and authorization. During this process, the delegation module consults the Resource to RunAs role mapping table to get the RunAs role (3). The delegation module consults the RunAs role to user ID and password mapping table to get the user that belongs to the RunAs role (4). The user ID and password is used to create a new credential using the authentication module, which is not shown in the figure.
![[IBM i]](../images/ngibmi.svg)
![[AIX Solaris HP-UX Linux Windows]](../images/ngdist.svg)