Security for the consumer (callout) scenario
Security support for the callout scenario is provided for messages from IMS to SOAP Gateway through
SSL, and from SOAP Gateway to the web service
through HTTPS.  You can also use the z/OS® Communications Server Application Transparent Transport Layer Security (AT-TLS) feature to secure messages in the callout scenario.
You can also use the z/OS® Communications Server Application Transparent Transport Layer Security (AT-TLS) feature to secure messages in the callout scenario. 
HTTPS encapsulates the SOAP messages from one point to another to prevent alteration to the exchanged messages. Although this level of security secures your messages and verifies your endpoints, it does not prevent execution of a web service by an unauthorized user.
- Basic authentication is supported by passing user name and password information in the connection bundle to the web service server. SOAP Gateway supports both the IbmX509 and SunX509 algorithms when they are configured with either the IBM® Java™ Runtime Environment (JRE) or Sun JRE that runs on the server that hosts the web service.
- WS-Security SAML confirmation method is supported for synchronous
callout applications by extracting the user ID (the user that initiates
the synchronous callout application) from the correlation token and
passing it to the external web service.Restriction: Security certificates for all external web service servers that IMS applications call out to must be stored in the same SOAP Gateway truststore because SOAP Gateway supports one truststore and one keystore per server instance.
- IMS V13 APAR PM96825
- IMS V12 APAR PM98017
SSL security, server authentication, and client authentication
You can use SSL security between IMS Connect and SOAP Gateway, and between SOAP Gateway and the external web services to provide security for the consumer scenario. Use of SSL on either side is optional and independent of the security setting on the other side.
- Create a truststore for SOAP Gateway to store the SSL server certificate from IMS Connect.
- Export the certificate from IMS Connect.
- Import the IMS Connect server certificate into the SOAP Gateway truststore.
When SSL security is used between SOAP Gateway and the web service, SOAP Gateway establishes security when it sends the IMS callout request to the external web service by using HTTPS. The server that hosts the web service sends back a certificate. After the transmission is secured and SOAP Gateway determines that the server certificate can be trusted, it executes the web service.
When calling out to an external web service by using HTTPS, specify the secure port as part of
the URI, even if the web service uses a default secure port such as 443 or 8443. Not including a
port will result in message IOGS043E. For example, the following URI is a valid external web service
callout using HTTPS: https://myexternalwebservice.com:443/service/MyWebService
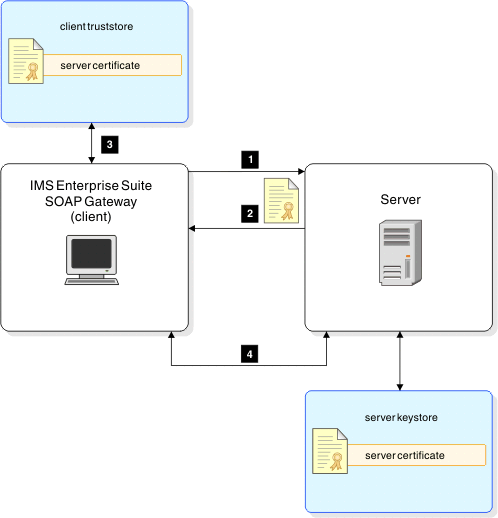
- The client (SOAP Gateway) initiates an HTTPS call.
- The web service server sends back a certificate.
- The client verifies the certificate with the server certificate stored in the truststore.
- After the transmission is secure, the client is allowed to execute the services.
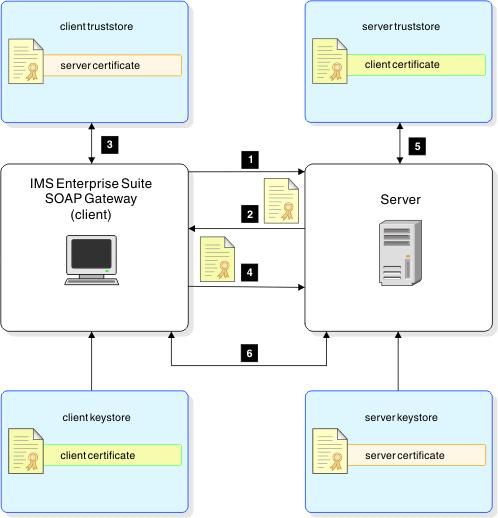
- The client initiates an HTTPS call.
- The server sends back a certificate.
- The client verifies the certificate with the server certificate that is stored in the truststore.
- The client sends the server a certificate.
- The server verifies the client certificate with the certificate that is stored in the truststore.
- After the transmission is secured, the client is authenticated and allowed to access protected services.
Basic authentication security scheme
Basic authentication means that the server that hosts the web service requires the client (SOAP Gateway) to have proper basic authentication credentials in order to invoke a service. The client transmits the credentials during the invocation of a web service.
The user ID and password for basic authentication are stored in the connection bundle. The user ID and password are specified when you generate the connection bundle for a callout web service by using the SOAP Gateway management utility. SOAP Gateway retrieves the pre-defined basic authentication security token from the connection bundle and passed it to external web service.
Basic authentication can be used with or without HTTPS. Without HTTPS, the user name and password information is transmitted in clear text.
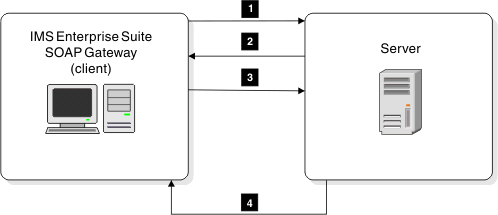
- The client (SOAP Gateway) initiates a request for the protected service.
- SOAP Gateway retrieves the basic authentication user ID and password information that is stored in the connection bundle.
- The web service server requests basic authentication information (user ID and password).
- The client sends the authentication information.
- After the transmission is secure, the server returns the requested service.
- Server and basic authentication
- Client authentication
- Client authentication and basic authentication