Setting a proxy connection on the server
When you install BigFix V9.2, you are asked if you want to set up communication with a proxy. If you did not configure the connection to the proxy at installation time or if you want to modify the existing configuration, you can edit the proxy configuration settings after installation by running the following command:
- On Windows systems:
%PROGRAM FILES%\BigFix Enterprise\BES Server\BESAdmin.exe /setproxy [/proxy:<proxy_host>[:<proxy_port>] [/user:<proxy_username> /pass:<proxy_password>] [/delete] [/exceptionlist:<proxy_exceptionlist>] [/proxysecuretunnel:{false|true}] [/proxyauthmethods:{basic|digest|negotiate|ntlm}] [/proxydownstream:{false|true}]] | [/delete]- On Linux systems:
/opt/BESServer/bin/BESAdmin.sh -setproxy [-proxy=<proxy_host>[:<proxy_port>] [-user=<proxy_username> -pass=<proxy_password>] [-exceptionlist=<proxy_exceptionlist>] [-proxysecuretunnel={false|true}] [-proxyauthmethods={basic|digest|negotiate|ntlm}] [-proxydownstream={false|true}]] | [-delete] | [-display]
- proxy
- It sets the host name or IP address and, optionally, the port number of the proxy machine. By default the value of proxy_port is 80.
- user
- It sets the user name that is used to authenticate with the proxy,
if the proxy requires authentication.
If you installed your BigFix server on a Windows system and your proxy requires Kerberos Authentication, use the format user@mydomain.com.
If your proxy requires NTLM Authentication, specify the NTLM user.
If your proxy requires the realm name notation, specify the proxy_user as user@mydomain.com or mydomain\user.Note: The Linux shell manages the back slash "\" as an escape character. Specify either mydomain\\user or "mydomain\user" to use the notation mydomain\user if you run the command in a Linux shell. - pass
- It sets the password that is used to authenticate with the proxy, if the proxy requires authentication. The value that is assigned to the password is encrypted in the registry on Windows systems or obfuscated in the configuration file on Linux systems.
- delete
- If specified, it deletes all the settings defined in BigFix for communicating with the specified proxy.
- display
- If specified, it displays the proxy communication settings defined in BigFix. This argument applies only to Linux systems.
- exceptionlist
- If set, it is a comma-separated list of computers, domains, and
subnetworks that must be reached without passing through the proxy.
In this syntax blank spaces have no influence. Each name in this list
is matched as either a domain, which contains the hostname, or the
hostname itself. For example, yourdomain.com would
match yourdomain.com, yourdomain.com:80,
and www.yourdomain.com, but not www.notyourdomain.com.
You can assign the following sample values to <proxy_exceptionlist>:
localhost,127.0.0.1, yourdomain.com localhost,127.0.0.1,yourdomain.com,8.168.117.0 "localhost,127.0.0.1, yourdomain.com, 8.168.117.0"By default, if you do not specify the exceptionlist setting, BigFix V9.2 prevents diverting internal communications from being diverted towards the proxy. This is equivalent to setting exceptionlist:localhost,127.0.0.1. To maintain this behavior, ensure that you add localhost, 127.0.0.1 to the list of exceptions when specifying the exceptionlist setting.
- proxysecuretunnel
- If set, it defines whether or not the proxy is enforced to attempt tunneling. By default the proxy does not attempt tunneling.
- proxyauthmethods
- If set, it restricts the set of authentication methods that can
be used. You can specify more than one value separated by a comma,
for example:
By default there is no restriction for the authentication method. The proxy chooses which authentication method must be used.proxyauthmethods:basic,ntlmNote: If you specify to use the negotiate authentication method on a Linux server or relay, a different authentication method might be used.Note: If you want to enable FIPS mode, ensure that the proxy configuration uses:- An authentication method other than digest on Windows systems.
- An authentication method other than digest, negotiate or ntlm on Linux systems.
- proxydownstream
- If set to true, this setting indicates that all HTTP communications
in your BigFix environment
also pass through the proxy. If you do not specify this setting, by
default the value false is assumed.Note: If you migrate an existing BigFix proxy configuration to V9.2 and the _Enterprise Server _ClientRegister _Proxy* keys are specified, by default proxydownstream is set to true.
On Windows servers the command BESAdmin.exe /setproxy opens the Proxy settings panel filled in the current proxy settings.
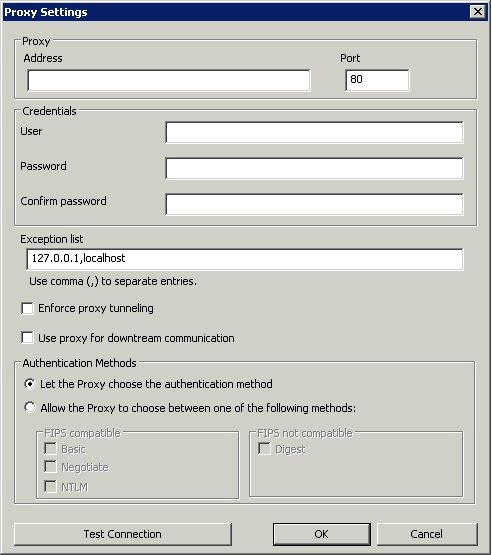
- On Windows systems:
- In the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\BigFix\EnterpriseClient\Settings\Client\.
- On Linux systems:
- In the [SOFTWARE\BigFix\Enterprise Server\Proxy] section of the besserver.config file.
For additional configuration settings that you can use to configure your BigFix environment, see Configuration Settings on the BigFix Wiki.