Troubleshooting
Problem
QRadar Vulnerability Manager authenticated scans for Microsoft Windows assets fail to complete the scan due to an authentication issue if SMBv1 is disabled on the Windows host.
Symptom
Authenticated scans for Windows hosts display an orange warning icon for assets where authentication failed in the Scan Results section of the Vulnerabilities tab. If this error message occurs, administrators who have the SMBv1 Protocol disabled can understand that the root cause of the failed scan. This issue impacts all versions of Microsoft Windows operating systems.
Environment
Administrators running QRadar Vulnerability Manager authenticated scans against Microsoft Windows assets, on all versions of QRadar with QRadar Vulnerability Manager enabled. This issue impacts all Microsoft operating systems where SMBv1 is disabled.
Diagnosing The Problem
How to verify your scan results for failed scans
- Log in to QRadar as an administrator.
- Click the Vulnerabilities tab.
- The Scan Results are be displayed.
- Review the list of scan results for Windows hosts.
- Optionally. From the Scan Results screen, click Search > New Search and run a search for recent scans with a Scan Status of Stopped or filter by Network Group for Windows hosts.
- Double-click the asset to view the asset details.
- Review the hover text for the following error message:
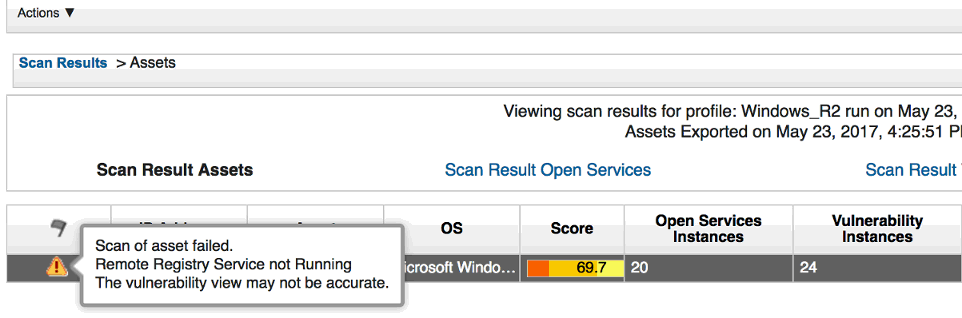
"Scan of asset failed
Remote Registry Service not Running
The vulnerability view may not be accurate"
Results
Screen capture showing the error message if SMBv1 Protocol is disabled on Windows hosts when the administrator runs an authenticated scan.
Resolving The Problem
For QRadar 7.2.x Administrators
There is currently no workaround for QRadar Vulnerability Manager at version 7.2.x. More communication will be issued in the future as a follow-up to resolve the SMBv1 Protocol issue. An APAR is being created for administrators to track this issue.
For QRadar 7.3.0 Administrators
A fix will be provided through QRadar Auto Update in the next few days to correct the scan issue for administrators at software version 7.3.0. Administrators that urgently need a fix for authenticated scans can apply the following workaround to enable SMBv2. If you are unsure of making this change, contact QRadar Support for assistance (http://ibm.biz/qradarsupport).
Warning: This workaround forces a minimum protocol version and allows administrators to successfully authenticate on Microsoft Windows assets where SMBv2 is enabled, but prevents QRadar Vulnerability Manager from being able to authenticate to assets that only have SMBv1 enabled. This workaround must be completed on all appliances where a QVM processor component or QVM scanner is deployed to successfully authenticate on Windows hosts that have SMBv2 configured. For more information on how to enable SMBv2, see: How to enable and disable SMBv1, SMBv2, and SMBv3 in Windows and Windows Server.
- Procedure
- Using SSH, log in to QRadar Console as the root user.
- Navigate to /opt/qvm/etc/.
- Edit the file smb.conf.
- Add the following line to the configuration file:
client min protocol = SMB2 - Save the changes to smb.conf. Note: No service restarts are required after the changes to smb.conf are saved.
- Repeat this process for any appliances that have a QRadar Vulnerability Manager processor deployed or on the scanner appliance itself.
- Administrators can restart Windows authenticated scans that failed after the change is made to all of the required appliances.
Results
After the file is saved, QRadar Vulnerability Manager scanners will use the configuration change and require authentication to Windows assets using SMBv2.
In QRadar 7.3.0, it is possible for administrators to change the configuration of QRadar Vulnerability Manager to use SMBv2 instead of SMBv1.
Where do you find more information?
Was this topic helpful?
Document Information
Modified date:
10 May 2019
UID
swg22004178