| Using File Access Definitions with Open Data Manager Introduction
This document describes how to setup Optim Open Data Manager (ODM)
to leverage the use of File Access Definitions (FAD).
The combination of these two Optim technologies provides a robust way
to secure archived data on an individual user basis down to the table
and column level of an archive file or collection.
The sections below detail how to configure ODM to use impersonation
so that ODBC credentials passed will be used to impersonate the end user.
In addition, the sections below also discuss the Operating System privileges
required for impersonated users to allow access to system objects
required for accessing archive files and collections.
This document is not intended to be a tutorial on the use of Optim, ODM, FAD,
or Operating System security.
It is intended to communicate the requirements and configuration
to facilitate the combined use of ODM and FAD only.
See the Prerequisites section below for additional information on skill sets
required to complete this configuration.
The use of the word "Optim" as it pertains to this document references the Optim Core distributed product. Prerequisites Skill Sets Required
Users of this document should be familiar with the configuration and operation of the following: - Optim Data Growth Solution
- Optim Open Data Manager (ODM)
- Optim File Access Definitions (FAD)
- Optim Access Control Domains (ACD)
- Operating System Administration and Security associated with your target platform
Software Requirements
The following software versions are the minimums needed to support the configuration described in this document. - Optim Data Grow Solution v7.3.1 or Higher
- Optim Connect v5.3 (As provided in the above Optim distribution)
OPEN DATA MANAGER AND FILE ACCESS DEFINITION OVERVIEW To leverage FAD via ODM, operating system impersonation is leveraged to represent client identity. As an example, when an ODBC connection parameter presents user credentials for John Doe, a process will be started on the server which will impersonate the user John Doe. In order to facilitate this, the main ODM process (Optim Connect Server daemon process) will first attempt to validate the user credentials provided for John Doe. If the process is unable to validate the user credentials (for any reason), the connection will be rejected. ODM consumes the underlying operating system security model to validate users. This requires that ODM user credentials must be valid credentials from the operating system's perspective. Credentials will be authenticated based on the following set of criteria. 1. If the ODM server resides in a domain, the user credentials will be validated against that domain.
2. If a domain is not available, the user credentials will be validated against the local user repository of the ODM server. EXCEPTION: In Windows kernel 5x environments, if a workgroup is defined on the machine where the ODM server is running, the workgroup name must be used in the FAD definition. The local user repository for which the ODM server is running will be used to validate the user. Once the user is validated, a sub process will be started which will impersonate the end user. As the impersonated user process attempts to access archive files and collections, the impersonated user credentials will be used to determine the level of access allowed to these resources. It is important to note that these interactions require configuration of both Optim and the underlying operating system. From an Optim perspective, the configuration involves allowing for user impersonation. From an operating system perspective, the configuration involves user management and access control. This separation of concern allows for leveraging the use of the underlying security model deployed within an enterprise.
FAD AND ODM CONFIGURATION There are three primary configurations required to enable FAD via ODM. 1. Operating System Credentials
2. Operating System File Permissions
3. Configuration of the ODM Server to Impersonate Users Operation System User Credential Requirement All users accessing an ODM data source which is FAD secured must have a valid account from the underlying operating systems perspective. The information provided in the section entitled "Open Data Manager and File Access Definition Overview", indicates one of the following requirements for user credentials. Windows kernel 5x - If the ODM Server is running within a Windows domain, users will be validated against that domain.
- If the ODM Server is running outside of a Windows domain, users will be validated against the local server's user repository.
UNIX Variants - If the ODM Server is running within a domain, users will be validated with that domain name against the local user repository.
- If the ODM Server is running outside of a domain, users will be validated with the server name against the local user repository.
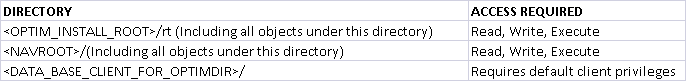
NOTE: Calls to the underlying OS to validate users is the same regardless if there is a domain present or not. Optim will prefix user names with a domain or machine name. It is up to the underlying OS to properly validate the user credentials. If the operating system on which the ODM Server is running has the ability to validate users against a central user repository, there will be no need to create local user credentials. In cases where the underlying operating system cannot validate against a central user repository, local user credentials will have to be created for ODM users. Operating System File Permissions - ODM User Credential Privileges Once the ODM Server has validated the user credentials, those credentials will require the appropriate file access to perform the operation of accessing Optim archives and collections. Listed below is the base set of file access permissions required by all ODM users for data sources secured by FAD.
 ODM / Optim Connect Server Configuration for Impersonation Configuration of the Optim Connect to support impersonation is a simple and straight forward process. Open Optim Connect Studio and expand the Machine tree to expose the workspaces associated with the data sources for which you want to configure impersonation. The default daemon (IRPCD) and workspace (Navigator) are shown below.
 Right click the workspace you want to configure, and select Open.
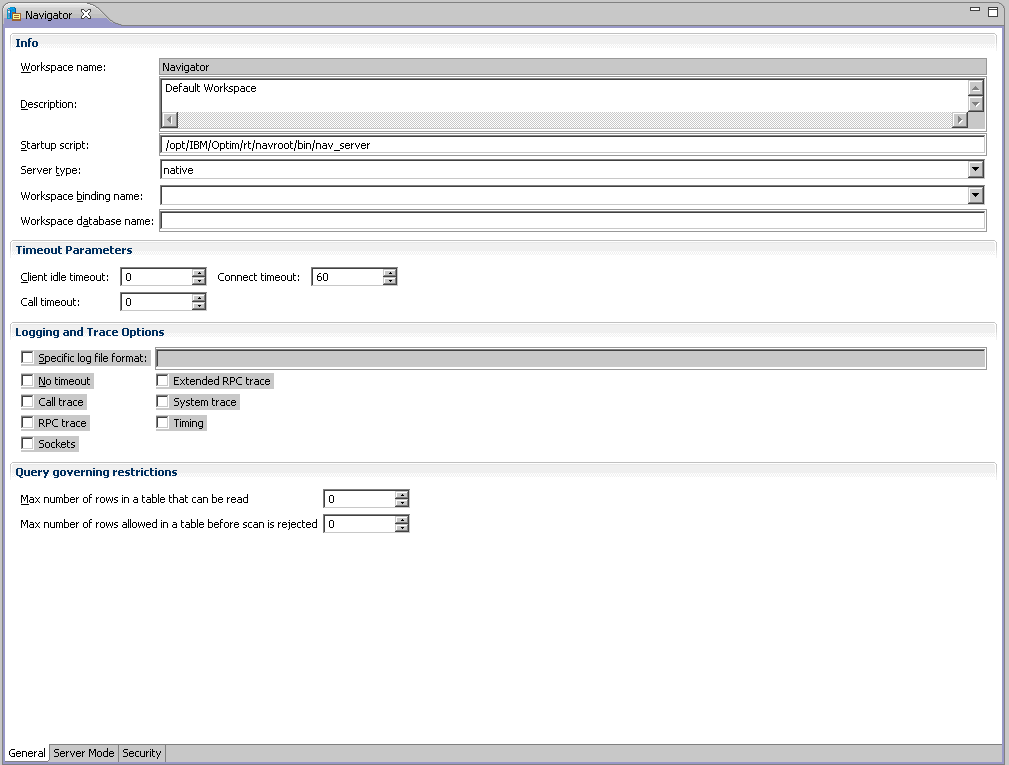
 This will open the workspace configuration editor with the General tab (tab at bottom of screen) in view. The General configuration screen should require no adjustments and look similar to the screen below.
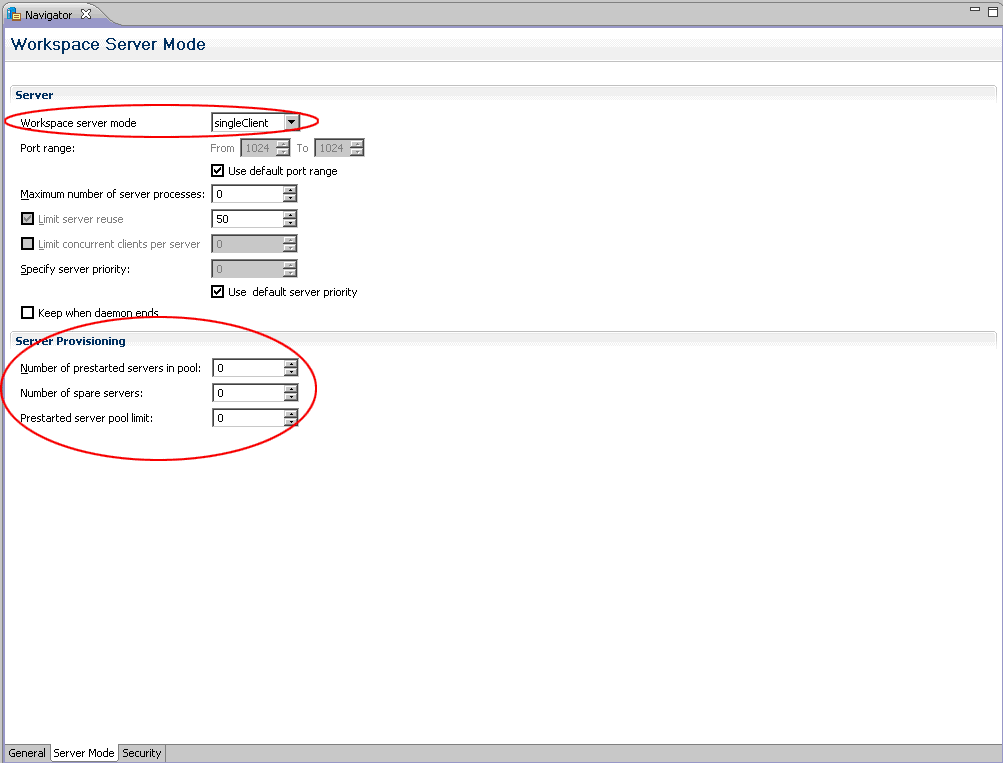
 Next, select the "Server Mode" tab in the workspace configuration editor. Under the "Server" section, ensure the "Workspace server mode:" is set to "singleClient". Under the "Server Provisioning" section, ensure all values are set to 0. Your configuration should look similar to the following screen shot.
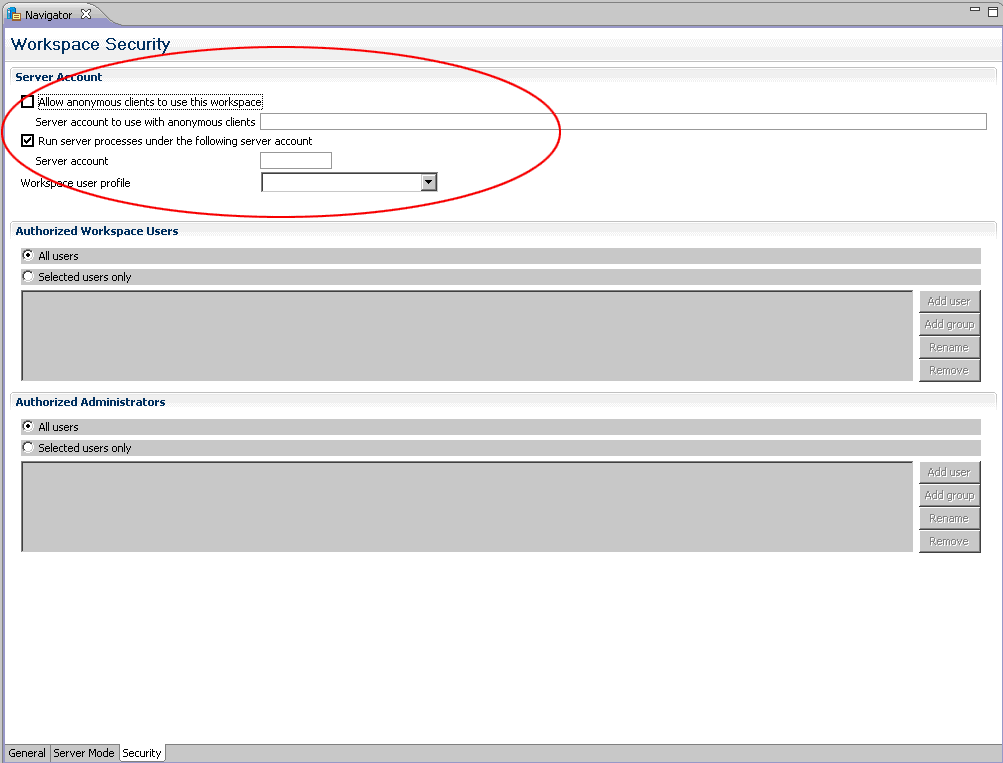
 Next, select the "Security" tab in the workspace configuration editor. Under "Server Account", do the following: 1. Uncheck "Allow anonymous clients to use this workspace".
2. Check "Run server processes under the following account". - For the "Server Account" input box needs to be empty. (Do NOT specify a server account.)
- For the "Workspace user profile" drop down list needs to be empty. (Do NOT specify a workspace user profile.)
Your configuration should look similar to the following screen shot.
 Now save the workspace configuration and reload the configuration on the server. See the section entitled "Runtime Requirements for Impersonation" for information on running the new configuration.
RUNTIME REQUIREMENTS FOR IMPERSONATION Once you have completed the configuration of a workspace to leverage impersonation, it is important to run the Optim Connect Server under a user ID that has authority to validate user credentials against the user repository in use. If the main Optim Connect Server daemon process ID does not have authority to validate users, all connections will be rejected. In addition, all users who connect to the server process will require the proper authority to read, write and execute various objects within the file system. Ensure that ALL users who will be connecting to the server and being impersonated have the proper access control writes as defined in the configuration section of this document. User credentials must be presented in the form of the simple UserID and Password. UserIDs must NOT include any domain qualification, as the user can only be impersonated within the domain for which the Optim Connect daemon is running. Only a simple UserID can be presented.
APPENDIX A UNIX EXAMPLE CONFIGURATION This appendix shows an example configuration for use with UNIX variants. It assumes that FAD and ODM are already installed and configured for normal user access. Users and Groups All users to be impersonated need to have local system accounts on the ODM server. It is typical that LDAP is leveraged to manage local users on UNIX variants within an enterprise. Take note if LDAP is deployed within your enterprise, as the creation of local users will be overwritten by LDAP if they are created locally. After you have determined the local user accounts are in place, create a group called "optim". Add all local user accounts to this group that will access ODM. File Permissions Locate the root installation directories for Optim and Optim Connect. Default location for Optim: /opt/IBM/Optim
Default location for Optim Connect: /opt/IBM/Optim/rt/navroot Optim Permissions
1. Change the GROUP recursively for the directory <OPTIM_INSTALL_ROOT>/rt to "optim" (created above). (e.g.: chgrp -R optim rt)
2. Change the GROUP permissions recursively for the directory <OPTIM_INSTALL_ROOT>/rt to READ, WRITE and EXECUTE (e.g.: chmod -R 755 rt) Optim Connect Permissions
NOTE: If Optim Connect is installed to the default location specified above, the previous step has already provided the group with the permissions needed. If it is NOT installed in the default location, perform the following. 1. Change the GROUP recursively for the directory <OPTIM_CONNECT_INSTALL_ROOT>/ to "optim" (created above).
2. Change the GROUP permissions recursively for the directory <OPTIM_CONNECT_INSTALL_ROOT>/ to READ, WRITE and EXECUTE Optim Directory Database Client
Next, locate the database client and change the group to "optim". Default privileges may or may not be sufficient depending on your client. Runtime Connections Start the Optim Connect Server
Start the Optim Connect Server with authority to validate users against the local user repository. (e.g.: root). Command: irpcd start Connect with ODBC Client
Using an ODBC client, connect to the ODM data source and provide valid user credentials. (e.g.: Username: odmuser1 Password: ******** Access Control Domains and FAD Definitions
Depending on the UNIX variant, the domain name listed in the Access Control Domain users list needs to specify either the hosts domain name OR the hostname itself as the domain name. (e.g.: localdomain or localhost) | 




