Question & Answer
Question
What steps do you need to follow to get Single Sign-On (Kerberos) working within WebSphere Lombardi Edition Version 7.1/7.2?
Answer
You might find steps in the installation and configuration guide. However, they are not as detailed as this document. This document contains the instructions and detailed steps to follow to install SSO (Kerberos) with WebSphere Lombardi Edition 7.1/7.2 on Windows successfully.
Prerequisites:
- You need to configure WebSphere Lombardi Edition 7.1/7.2 to integrate successfully with your LDAP provider first. See the "Configuring an LDAP security provider" section in the Process Center Installation and Configuration guide on page 13.
- A known issue exists whereby communication between the Process Center and Runtime Servers is affected after SSO (Kerberos) is configured. Install Hotfix 100827710 to address this issue. You can request this HotFix by opening a PMR with WebSphere Lombardi Edition support team and requesting HotFix 100827710. See the section with the Hotfix installation steps near the end of this document.
Configuring SSO (Kerberos)
Use the following steps to configure SSO (Kerberos):
- On the domain controller, create a new Active Directory user, which is used to map to the Kerberos service principal name (SPN) for IBM WebSphere Application server.
- On the domain controller, navigate to Start > Administrative Tools > Active Directory Users and Computers.
- Create a user account, wle_spn and ensure that the Use Kerberos DES encryption types for this account option is not checked.
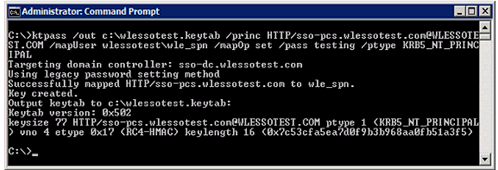
- From the domain controller, create the Kerberos keytab file using the following command:
ktpass –out <keytab file> –princ <FQDN principal of WLE server with realm> –mapUser <domain user to map SPN> –mapOp set –pass <password> –ptype KRB5_NT_PRINCIPAL
For example:
ktpass –out c:\wlessotest.keytab –princ HTTP/sso-pcs.wlessotest.com@WLESSOTEST.COM –mapUser wlessotest\wle_spn –mapOp set –pass testing –ptype KRB5_NT_PRINCIPAL
On Windows Server 2008, the switches are denoted using “/” instead of “-“:
ktpass /out c:\wlessotest.keytab /princ HTTP/sso-pcs.wlessotest.com@WLESSOTEST.COM /mapUser wlessotest\wle_spn /mapOp set /pass testing /ptype KRB5_NT_PRINCIPAL
- Copy the newly created keytab file from the domain controller to the IBM WebSphere Application Server.
- From the IBM WebSphere Application/WebSphere Lombardi Edition server, run the following command to check if the SPN has been registered:
setspn –L wle_spn
If the SPN does not show, then run the following command from the IBM WebSphere Application/WebSphere Lombardi Edition server to register the SPN:
setspn –A HTTP/sso-pcs.wlessotest.com wle_spn

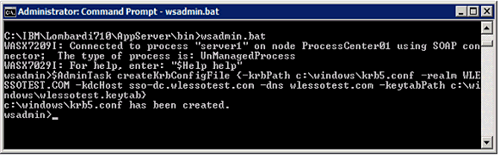
- Generate the krb5.conf file by following these steps:
- On the WebSphere Lombardi Edition server, navigate to (WLE_HOME)\AppServer\bin and run wsadmin.bat, log in with tw_user if prompted.
- Run this command to create the krb5.conf file:
$AdminTask createKrbConfigFile {-krbPath <path to krb5.conf> -realm <realm> -kdcHost <domain controller FQDN> –dns <domain> -keytabPath <path to keytab>}
$AdminTask createKrbConfigFile {-krbPath c:\windows\krb5.conf -realm WLESSOTEST.COM -kdcHost sso-dc.wlessotest.com –dns wlessotest.com -keytabPath c:\windows\wlessotest.keytab}
- Open the file and check that it looks similar to this:
[libdefaults]
default_realm = WLESSOTEST.COM
default_keytab_name = FILE:c:\windows\wlessotest.keytab default_tkt_enctypes = rc4-hmac des-cbc-md5
default_tgs_enctypes = rc4-hmac des-cbc-md5
forwardable = true
renewable = true
noaddresses = true
clockskew = 300
[realms]
WLESSOTEST.COM = {
kdc = sso-dc.wlessotest.com:88
default_domain = wlessotest.com
}
[domain_realm]
.wlessotest.com = WLESSOTEST.COM - Configure SPNEGO Web Authentication by following these steps:
- Open the IBM WebSphere Application server administrative console and navigate to Global security > Authentication > Web and SIP security > SPNEGO Web authentication.
- Under SPNEGO Filters, click New.
- Enter the Host name as the fully qualified domain name of the WebSphere Lombardi Edition Server, the Kerberos realm name, enter the Filter criteria of: request-url^=ProcessCenter|ProcessAdmin|portal, and finally ensure that Trim Kerberos realm from principal name is checked and Enable delegation of Kerberos credentials is not checked. Once all settings are in place, click OK and then click Save directly to the master configuration at the top of the screen.
Note: The filter is case sensitive – be sure to enter it exactly as shown above – and the specified values above will enable SSO for each of the web applications in the list, remove an entry to disable SSO for that application.

- In the IBM WebSphere Application server administrative console, go to Global Security->Authentication->Web and SIP security->SPNEGO Web authentication, then check Dynamically update SPNEGO and Enable SPNEGO, then add the Kerberos configuration and keytab file paths in their respective places, finally click OK and click Save directly to the master configuration at the top of the screen.

- Restart the IBM WebSphere Application server and WebSphere Lombardi Edition services.
IMPORTANT NOTE:
After making the above changes, the WebSphere Administrative Console might change the authentication mechanism on the Global security screen from LTPA to LTPA and Kerberos. Make sure that only LTPA is selected unless the environment has the internal WebSphere Lombardi Edition users (tw_user, tw_admin, etc) setup in the LDAP and you use Standalone LDAP configuration in WebSphere and not Federated repository. In this case, LTPA and Kerberos is required (See the following screen shot).

After SSO is applied to Process Centers, they will not be able to communicate with attached runtime environments – the status will show as “Connected? (This server may not be available right now.)” and snapshots cannot be installed. To remedy this, apply the hotfix WLE-7.1.0-HotFix-100827710.zip by following the instructions below:
- Copy the WleSpnegoFilter.jar file included in the hotfix to the following directory on the Process Center machine only: (WLE_HOME)\AppServer\lib\ext\
- Restart the WebSphere Administrative Console service so that it can reference the jar file as listed in the previous step.
- Open the IBM WebSphere Application server administrative console and navigate to Global security->Authentication->Web and SIP security->SPNEGO Web authentication.
- Under SPNEGO Filters:, edit the filter that was created during SSO configuration showing a filter criteria of: request-url^=ProcessCenter|ProcessAdmin|portal
- Delete the existing filter criteria and instead only put: .*dummy.html
- In the Filter class:, enter: com.lombardisoftware.security.filter.spnego.WleSpnegoFilter
- Restart the WebSphere services and WebSphere Lombardi Edition services on the Process Center.
- Check the Servers tab from the Authoring Environment or Process Center console and the connected runtime servers should show as Connected.
IMPORTANT NOTE: If you have Fix Pack 1 for WebSphere Lombardi Edition V7.1 installed or if you are running WebSphere Lombardi Edition 7.2, you do not need to install the mentioned HotFix. This issue is resolved in WebSphere Lombardi Edition V7.1.0.1 (WebSphere Lombardi Edition 7.1 Fix Pack 1) and WebSphere Lombardi Edition V7.2
Configuring SSO in Clustered Environments
In addition to the configuration outlined previously, the following steps must be taken to successfully configure SSO in a clustered WebSphere Lombardi Edition environment:
- A separate LDAP account must be created for each node. For a two-node cluster, there should be two user accounts created. For example, wlessoprod01 and wlessoprod02.
- A separate keytab file must be created for each node in the cluster.
- All keytab files within the node should be merged using the following command:
(WLE_Installer_Home)/was-iip-jdk/jre/bin/ktab -m <keytab file1> <keytab file2>
This command will merge both keytab files into <keytab file2>
- Copy the merged keytab file to the same location on all nodes.
- Copy the krb5.ini file to the same location on both all nodes.
- From the WebSphere Application Server Administrative console, create a new SPNEGO filter for each additional node.
- Save and synchronize the changes manually for all nodes.
Configure Microsoft Internet Explorer Browser to Allow Single Sign-On (SSO)
The following steps are required to allow Internet Explorer to log a user in using single sign-on (SSO):
- In Internet Explorer, go to Tools->Internet Options->Security->Local intranet->Sites->Advanced option and add the FQDN of the WebSphere Lombardi Edition server.
- Go to the Tools->Internet Options->Advanced tab and ensure that the Enable Integrated Windows Authentication option under the Security section is selected.
- Close and re-open the browser.
- Navigate to the WebSphere Lombardi Edition server and ensure that single sign-on is working.
Configure Mozilla Firefox Browser to Allow Single Sign-On (SSO)
The following steps are required to allow Mozilla Firefox to log a user in using single sign-on (SSO):
- In Firefox, enter about:config in the browser address field.
- Type network.n in the filter field.
- Double-click the preference network.negotiate-auth.trusted-uris and add the host names in a comma-delimited string to enable SPNEGO authentication, for example: http://sso-pcs.wlessotest.com,http://sso-ps.wlessotest.com
- Click OK.
- If the SPNEGO solution uses the advanced Kerberos feature of credential delegation, double-click network.negotiate-auth.delegation-uris to list the sites for which the browser can delegate user authorization to the WebSphere Lombardi Edition server, for example: http://sso-pcs.wlessotest.com,http://sso-ps.wlessotest.com
- Click OK.
- Click OK and the configuration displays as updated.
- Restart the Firefox browser to activate this configuration and ensure that single sign-on is working.
Disable SPNEGO SSO
To disable the WebSphere Lombardi Edition SPNEGO single sign-on functionality without removing all settings, follow these instructions:
- Open the WebSphere Administrative Console (typically https://localhost:9043/ibm/console).
- In the left-hand navigation pane, go to Security -> Global security -> Web and SIP
security -> SPNEGO Web authentication. - Clear the Enable SPNEGO checkbox to disable SSO.
- Restart all WebSphere and WebSphere Lombardi Edition services to apply the change.
Product Synonym
WLE 7.1 7.2
Was this topic helpful?
Document Information
Modified date:
15 June 2018
UID
swg21448203