Question & Answer
Question
How to determine the SSL/TLS protocol and cipher suite used for each active System TLS connection to the IBM i
Answer
The Trace Licensed Internal Code (LIC) service tool is used to capture a System TLS trace point that contains this information. The Trace Internal (TRCINT) command is the command interface to the Trace LIC Service tool.
*****************
Prior to performing the following steps, make sure that the following PTFs are applied to the system first:
610- MF59767
611- MF59784
710- MF59800
720- MF59777, MF67576
730 - MF67575
740 - MF67574
*****************
To trace all SSL/TLS protocol versions issue the following command to start the trace
TRCINT SET(*ON) TRCTBL('SSL-1700x') TRCTYPE(*SCKSSL) SLTTRCPNT((17000 17009))
Wait the desired period of time for new SSL/TLS connections to establish and end the trace with the command ;
TRCINT SET(*OFF) TRCTBL('SSL-1700x') OUTPUT(*PRINT)
To delete the trace issue the following command;
TRCINT SET(*END) TRCTBL('SSL-1700x')
If you want to limit the trace and find only specific SSL/TLS protocol version connections use one or more of the following trace points
|
Protocol
Version |
Trace
Identifier |
| TLSv1.3 | 17005 |
| TLSv1.2 | 17004 |
| TLSv1.1 | 17003 |
| TLSv1.0 | 17002 |
| SSLv3 | 17001 |
| SSLv2 | 17000 |
For example to find only SSLv3 connections use trace point 17001
TRCINT SET(*ON) TRCTBL('SSL-17001') SIZE(128000) TRCTYPE(*SCKSSL) SLTTRCPNT((17001))
For a range of SSL versions specify the beginning Trace ID followed by the end Trace ID, for example SSLv2 through TLSv1.0
TRCINT SET(*ON) TRCTBL('SSL-1700x') SIZE(128000) TRCTYPE(*SCKSSL) SLTTRCPNT((17000 17002))
A spooled file named QPCSMPRT will be created for the user that ran the TRCINT SET(*OFF).
Below is an example output for one connection.
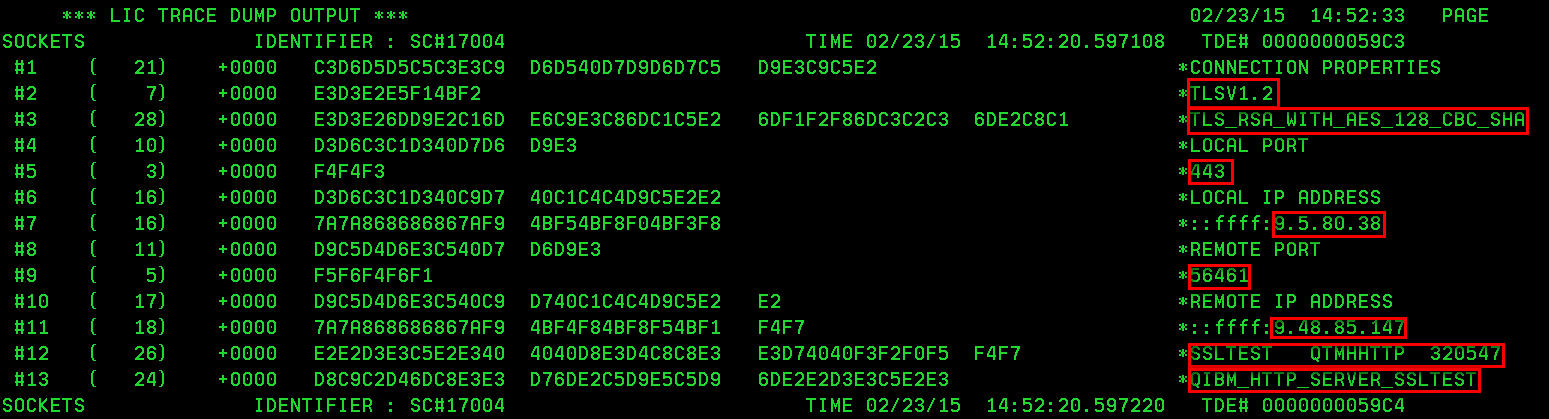
You can see the first highlight is the SSL/TLS version followed by the cipher suite that was negotiated with this connection.
Next the IP information of the local and remote IP and port pair is displayed.
The last two highlights are the local job information and the SSL/TLS application ID if used in DCM.
With this information we see that this connection is using TLSv1.2 and TLS_RSA_WITH_AES_128_CBC_SHA cipher and was for port 443. The job and APP ID tell us that it's an Apache server.
Depending on how the application is setting up the SSL/TLS environment you may not see a job name and number but a task instead, but with the other information it should be enough to determine what application is being accessed on the IBMi.
[{"Line of Business":{"code":"LOB57","label":"Power"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"SWG60","label":"IBM i"},"ARM Category":[{"code":"a8m0z0000000CHyAAM","label":"Security"}],"Platform":[{"code":"PF012","label":"IBM i"}],"Version":"7.1;7.2;7.3;7.4"}]
Was this topic helpful?
Document Information
Modified date:
14 January 2022
UID
nas8N1020594