Troubleshooting
Problem
This note documents the steps to take when moving to security level 40 from a lower level.
Resolving The Problem
According to the Security Reference manual, before moving from security level 30 to security level 40, you should turn on security auditing to find any trouble spots. This document describes how to turn on auditing and analyze the results.
Chapter 2 of the Security Reference manual, suggests paying particular attention to the following Authority Failure (AF) violation types:
B Restriction (blocked) instruction violation
C Object validation failure
D Unsupported interface (domain) violation
J Job-description and user-profile authorization failure
R Attempt to access protected area of disk (enhanced hardware storage protection)
S Default sign-on attempt
Turning on Security Auditing
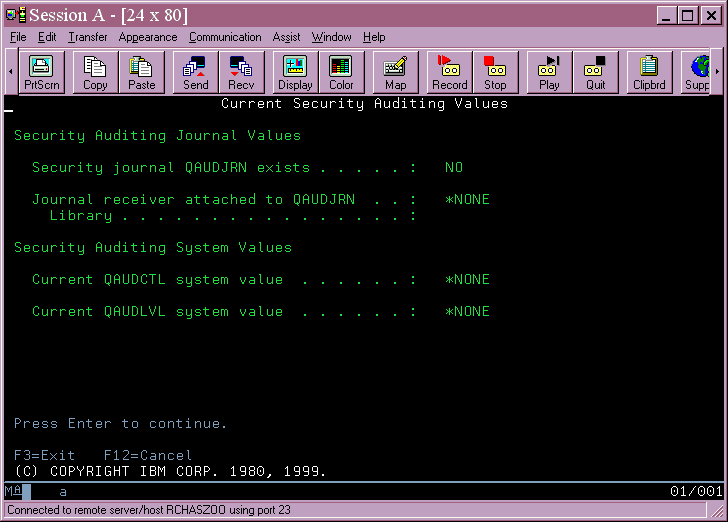
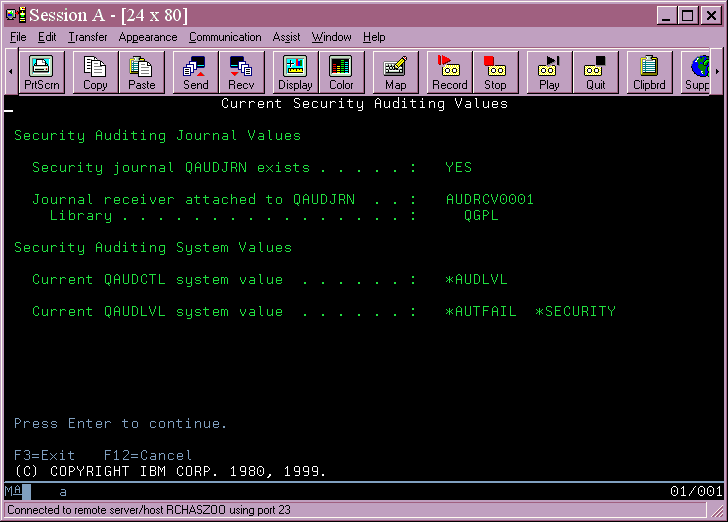
If you already have security auditing turned on, you must only ensure the QAUDLVL system value contains *AUTFAIL & *PGMFAIL and the QAUDCTL system value includes *AUDLVL. If you do not have auditing turned on, the steps described in the Security Reference manual, Chapter 9, Auditing Security on the AS/400 System, under the section titled Setting up Security Auditing, are reproduced here:
Chapter 2 of the Security Reference manual, suggests paying particular attention to the following Authority Failure (AF) violation types:
B Restriction (blocked) instruction violation
C Object validation failure
D Unsupported interface (domain) violation
J Job-description and user-profile authorization failure
R Attempt to access protected area of disk (enhanced hardware storage protection)
S Default sign-on attempt
Turning on Security Auditing
If you already have security auditing turned on, you must only ensure the QAUDLVL system value contains *AUTFAIL & *PGMFAIL and the QAUDCTL system value includes *AUDLVL. If you do not have auditing turned on, the steps described in the Security Reference manual, Chapter 9, Auditing Security on the AS/400 System, under the section titled Setting up Security Auditing, are reproduced here:
| To set up security auditing, you can either use the GO SECTOOLS menu or set it up manually. Both methods are described below. You only have to use one or the other. Setting up auditing requires *AUDIT special authority. Using GO SECTOOLS to turn on Security Auditing:
 To manually set up auditing, you can use these steps: 1 Create a journal receiver in a library of your choice by using the Create Journal Receiver (CRTJRNRCV) command. This example uses a library called JRNLIB for journal receivers.
Place the journal receiver in a library that is saved regularly. Choose a journal receiver name that can be used to create a naming convention for future journal receivers, such as AUDRCV0001. You can use the *GEN option when you change journal receivers to continue the naming convention. Using this type of naming convention is also useful if you choose to have the system manage your journal receivers. Specify a receiver threshold appropriate to your system size and activity. The size you choose should be based on the number of transactions on your system and the number of actions you choose to audit. If you use system journal management support, the journal receiver threshold must be at least 5,000KB. The default is 1,500,000. For more information on journal receiver threshold refer to the Backup and Recovery book. Specify *EXCLUDE on the AUT parameter to limit access to the information stored in the journal. 2 Create the QSYS/QAUDJRN journal by using the Create Journal (CRTJRN) command:
The name QSYS/QAUDJRN must be used. Specify the name of the journal receiver you created in the previous step. Specify *EXCLUDE on the AUT parameter to limit access to the information stored in the journal. You must have authority to add objects to QSYS to create the journal. Use the Manage receiver (MNGRCV) parameter to have the system change the journal receiver and attach a new one when the attached receiver exceeds the threshold specified when the journal receiver was created. If you choose this option, you do not have to use the CHGJRN command to detach receivers and create and attach new receivers manually. Do not have the system delete detached receivers. Specify DLTRCV(*NO), which is the default. The QAUDJRN receivers are your security audit trail. Ensure that they are adequately saved before deleting them from the system. The Backup and Recovery book provides more information about working with journals and journal receivers. 3 Set the audit level (QAUDLVL) system value using the WRKSYSVAL command. The QAUDLVL system value determines which actions are logged to the audit journal for all users on the system. |
For purposes of auditing in preparation for moving to security level 40, the system value QAUDLVL should contain audit value *AUTFAIL & *PGMFAIL. Steps 4 through 8 do not concern us for this document; however, it is suggested that you read the whole chapter to be familiar with security auditing.
| 9 Start auditing by setting the QAUDCTL system value to a value other than *NONE. The QSYS/QAUDJRN journal must exist before you can change the QAUDCTL system value to a value other than *NONE. When you start auditing, the system attempts to write a record to the audit journal. If the attempt is not successful, you receive a message and auditing does not start. |
The QAUDCTL system value needs to be set to *AUDLVL to use the *AUTFAIL & *PGMFAIL value in the QAUDLVL system value. Once you set that, the system begins logging security.
Reading the Security Journal
There are several ways to read the security journal. This section will describe looking at it interactively. The next section will describe creating a report using Query.
To look at the security journal, use the Display Journal command:
DSPJRN JRN(QSYS/QAUDJRN) ENTTYP(AF)
QSYS/QAUDJRN is the security journal, and AF journal types are Authority Failure records. *PGMFAIL audit entries are recorded as AF journal entries. This command will produce a screen like this:
|
This is a list of audit journal entries. Typing 5 (Display) next to the last entry shows the following screen:
|
Looking in Appendix F of the Security Reference manual, there is a description of the "AF" entry. It says the first character is the type of violation, in this case D which means "Use of unsupported interface, object Domain failure." The object that was being accessed is next, QSPWRKF from library QSYS, a program. Then the job, name QPADEV0009, user TROLL, job number 103522. (I know from experience that we do not need the rest of the information.) Pressing F10 gives the journal entry details, which looks similar to the following:
|
The job and the time the journal entry was created shown. If we look for this job, we should see what was happening at that time. Get a copy of the job log. (If you need help with getting the job log, see document Primer on Message Analysis.
In this case, the job log looks similar to the following.
Note: The columns have been compressed to better fit on the paper.
|
At the time of the audit record, the user was running command WS. It turns out that this is just a duplicate of the WRKSPLF command, created to be easier to type. This command was initially created with the command:
CRTDUPOBJ OBJ(WRKSPLF) FROMLIB(QSYS) OBJTYPE(*CMD) TOLIB(QGPL) NEWOBJ(WS)
A change to the WS command in the past caused it to lose *SYSTEM state. Since the command processing program that this command calls is the IBM program QSPWRKF and is a *SYSTEM domain program, the command causes the AF audit record to be issued, and would cause the command to fail if the system went to security level 40.
If you check table 2-3 in the Security Reference manual, this falls under the case of an IBM-supplied command that was changed to run a different program, then changed back to run the original program. (Although WS has a different name, the CRTDUPOBJ command duplicated it in such a way that the system considered it an IBM command.) If you look at the command (DSPCMD) before such a change you will see that the " State used to call program" attribute is set to *SYSTEM. After the change the state has changed to *USER. A *USER state command cannot call a system domain object at security level 40.
This procedure will help you find the program or application that will not work when you change to security level 40. It will then be up to the application developer to modify the program to work at security level 40.
To view the audit records via a query please do the following:
If the system is at V530 or above, follow the instructions below. If the system is at V520 or an earlier release, the name of the output file and the type is different (QASYAFJ4 for V520).
First, generate an output file to query using the following commands:
CRTDUPOBJ OBJ(QASYAFJ5) FROMLIB(QSYS) OBJTYPE(*FILE) TOLIB(QGPL)
DSPJRN JRN(QAUDJRN) ENTTYP(AF) OUTPUT(*OUTFILE) OUTFILFMT(*TYPE5) OUTFILE(QGPL/QASYAFJ5)
Then, use the STRSQL or RUNQRY command to create the query. Do the following:
| 1. | Run the STRSQL command, and press the Enter key. |
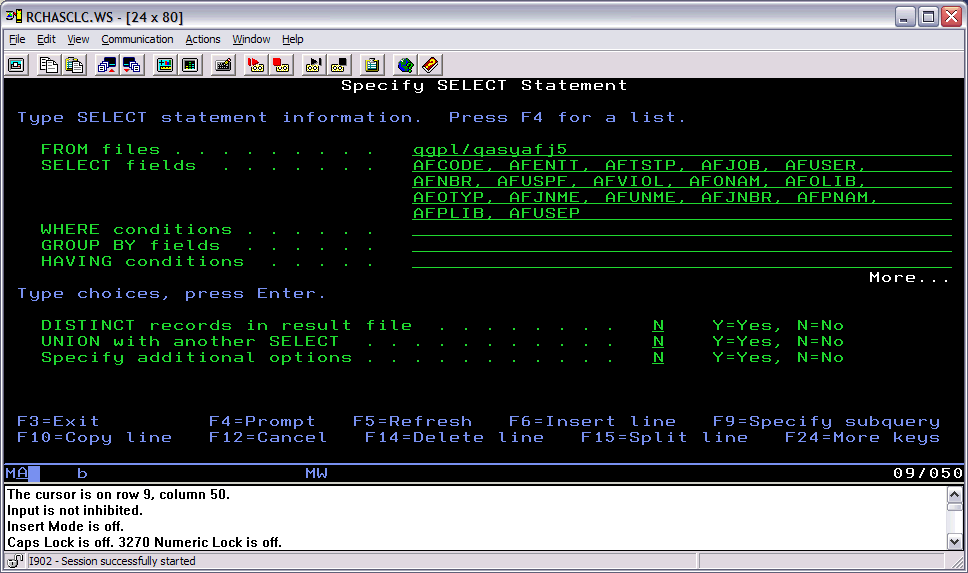
| 2. | Type Select, and press F4. |
| 3. | Fill out the Specify SELECT Statement as follows: Add or delete fields as desired. Some of the basic fields to analyze AF entries are includeds below. |
To use Query rather than SQL, do the following:
| 1. | From the operating system command line, run the following command: STRQRY |
| 2. | Select Option 1, Work with Queries. |
| 3. | Select Option 1, Create Query. |
| 4. | Type 1 in front of specify file selections, press enter |
| 5. | Type in QASYAFJ5 for file and QGPL for Library, and pres the Enter key two times. |
| 6. | Type 1 in front of select and sequence fields. Put 1, 2, 3, 4 and so on in front of the fields that you would like. See below for an example: |
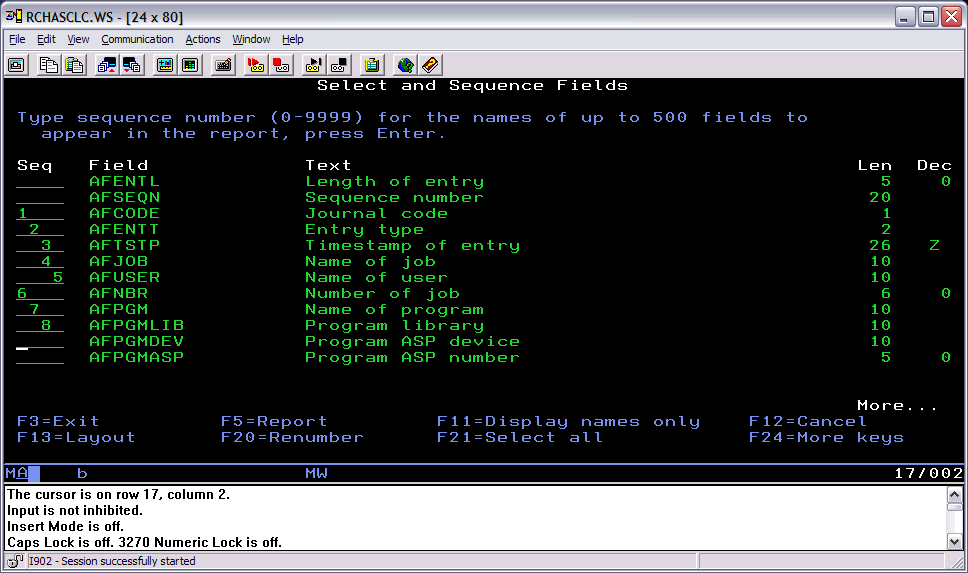
| 7. | Press the Enter key two times. |
| 8. | Press F3 to save and run the query. |
[{"Type":"MASTER","Line of Business":{"code":"LOB57","label":"Power"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"SWG60","label":"IBM i"},"ARM Category":[{"code":"a8m0z0000000CHyAAM","label":"Security"}],"ARM Case Number":"","Platform":[{"code":"PF012","label":"IBM i"}],"Version":"6.1.0;7.1.0;7.2.0"}]
Historical Number
13354737
Was this topic helpful?
Document Information
Modified date:
22 March 2023
UID
nas8N1019668