Troubleshooting
Problem
This document describes how to use SSH tunneling as a secure connection to Telnet.
Resolving The Problem
SSH Tunneling can be used as encryption service to applications that currently do not have SSL abilities.
One limitation to SSH Tunneling is that a session must be open for each port you want to forward over the connection.
To use the IBM i family of servers as a SSH Client of a remote SSH service for the purposes of tunneling, do the following:
| 1. | On the client, start an SSH session to the server (named servername in this example) that will route the traffic on an unused port on the client (50000 in this example) to the Telnet port (23) on the server: CALL QP2TERM Press the Enter key. |
| 2. | On the PASE command line, type the following: ssh -T -L50000:localhost:23 servername Press the Enter key. This SSH session must be left active while the Tenet sessions are in use. |
| 3. | Run the following command to connect to remote system: TELNET RMTSYS('127.0.0.1') PORT(50000) Press the Enter key. |
Unix and PC clients can connect securely to Telnet or any other service using SSH Tunneling.
The following example is of a Unix system connecting to the IBM iSeries family of servers system by starting a tunnel SSH session, and then connecting with Telnet to the iSeries family system over the tunnel.
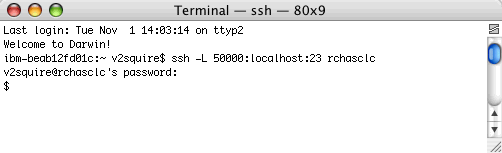
Then Telnet to the machine by specifying the IP as 127.0.0.1 and the port as 5000.
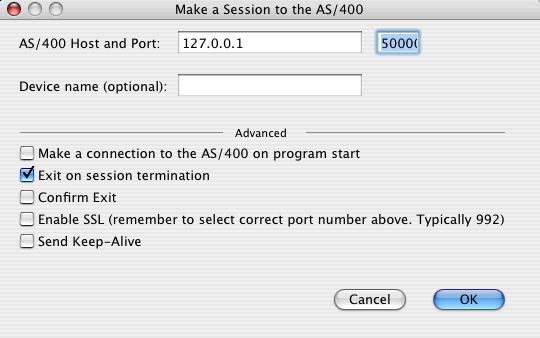
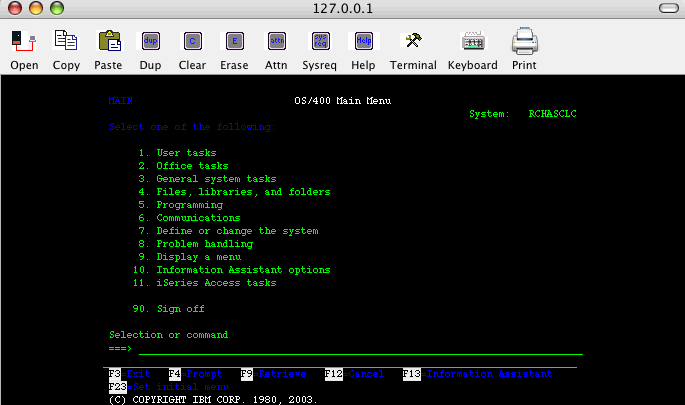
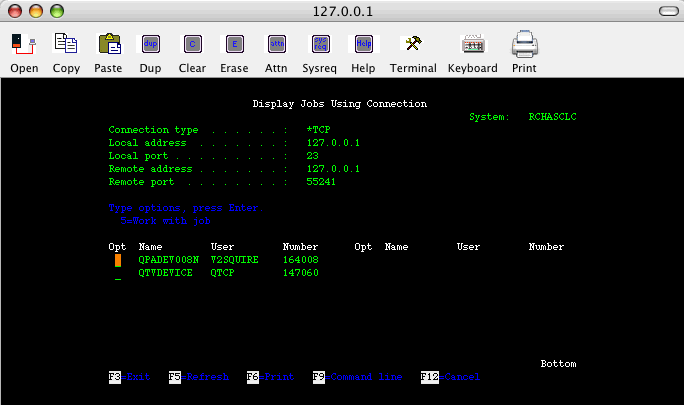
Run the NETSTAT *CNN command to verify that your connection is being tunneled through SSH.
Note: Your local client will have a loopback listening on port 50000. The remote server system has a different client port number on loopback hosting your session. In this example, it is port 55241.
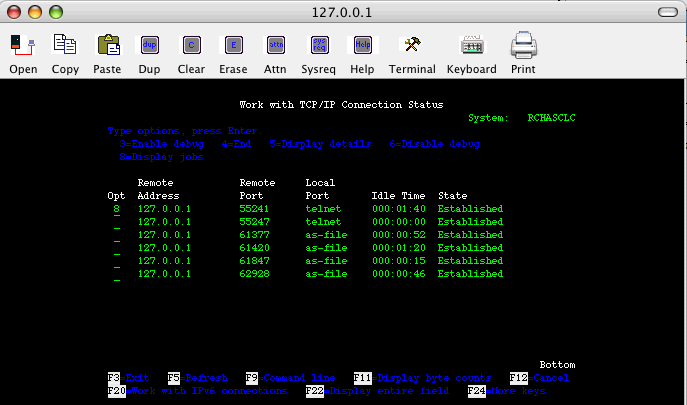
Select Option 8 on the loopback resource that shows the local port as Telnet. You will see your user job.
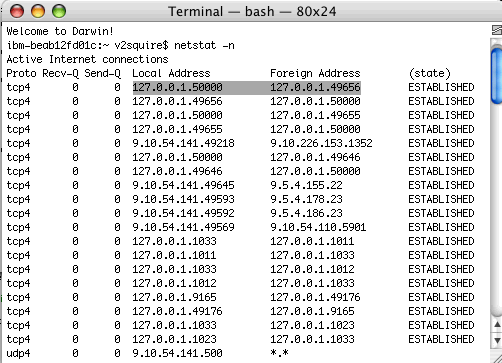
Running the netstat -n command on the Unix system shows you your current connections.
For additional information, refer to the following Web sites:
www.openssh.org
www.hackinglinuxexposed.com/articles/20030228.html
http://www-03.ibm.com/servers/enable/site/porting/tools/openssh.html
[{"Product":{"code":"SWG60","label":"IBM i"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Component":"Communications-TCP","Platform":[{"code":"PF012","label":"IBM i"}],"Version":"Version Independent","Edition":"","Line of Business":{"code":"LOB57","label":"Power"}}]
Historical Number
395029015
Was this topic helpful?
Document Information
Modified date:
18 December 2019
UID
nas8N1015260