Troubleshooting
Problem
This document includes steps to configure the IBM i FTP server to use SSL/TLS.
Resolving The Problem
NOTE: This document includes steps to configure the IBM i FTP server to use SSL/TLS using Heritage Digital Certificate Manager. If you would like to use the updated Digital Certificate Manager see the following documentation:
Use the following steps to configure the iSeries FTP server to use SSL/TLS. This document was created under the assumption that the user has already accessed Digital Certificate Manager (DCM) and has already either purchased a third-party certificate, or has created their own certificate to assign to the FTP server.
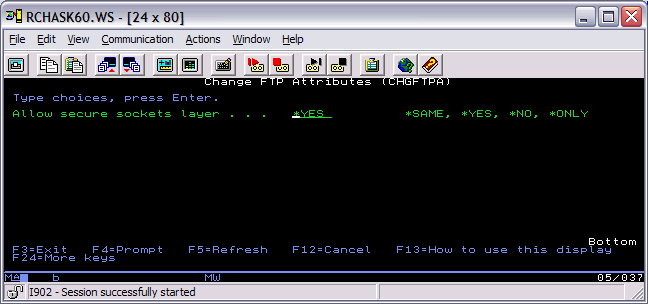
1. In the CHGFTPA screen (F4 to prompt this command), set the Allow secure sockets layer option to *YES. The *ONLY option will also allow SSL/TLS FTP connections; however, it will not allow regular non-secure connections to come through. After making the change, restart the FTP server (ENDTCPSVR *FTP and then STRTCPSVR *FTP).
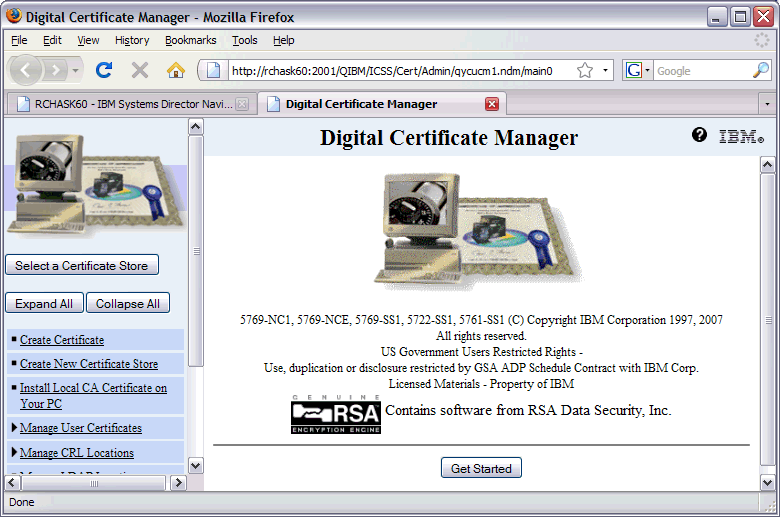
2. Go to the Digital Certificate Manager application to assign a certificate to the FTP server application ID. You will need to make sure the HTTP Admin server is active and that it can be accessed. In the QHTTPSVR subsystem, there should be an ADMIN job. If Admin is not active, use the command STRTCPSVR SERVER(*HTTP) HTTPSVR(*ADMIN) to start it. The Admin page can be accessed by going to http://<systemname or IP address>:2001/QIBM/ICSS/Cert/Admin/qycucm1.ndm/main0
3. Click on the Select a Certificate Store button and choose the *SYSTEM store. Enter your store password when it prompts you (this was created by the individual who created the *SYSTEM store).
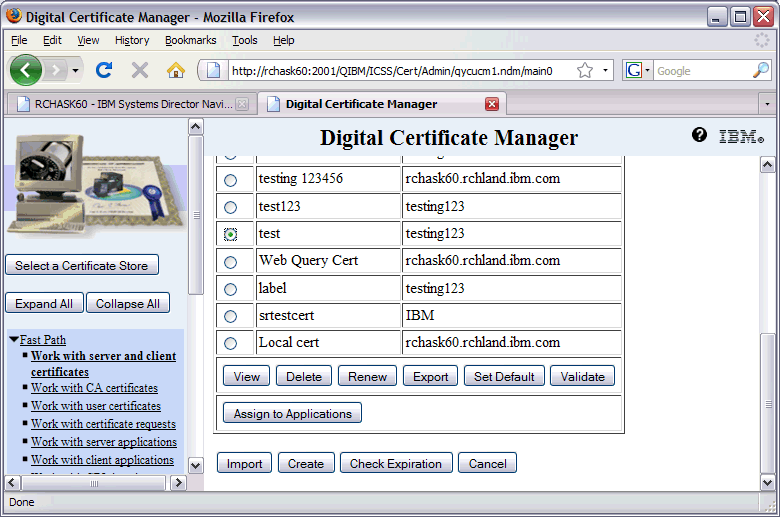
4. Once you are signed in, choose the Fast Path option, then select Work with server and client certificates. You will see the certificates you have to choose from on the right-hand side. Select the one you want to assign to the FTP server and click Assign to Applications.
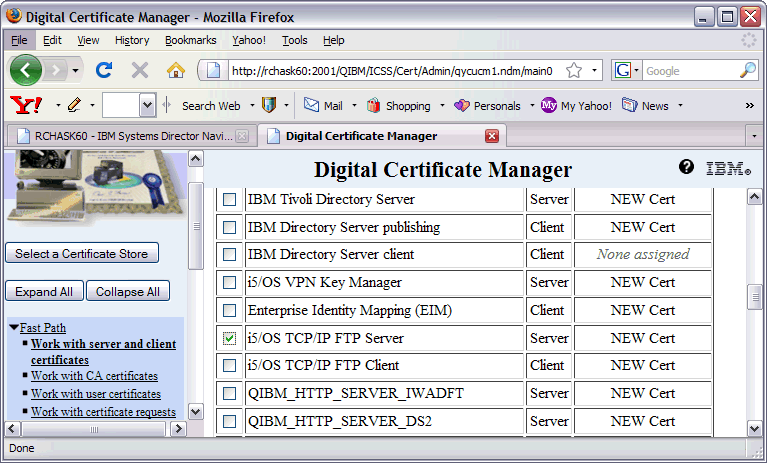
5. Check the box for i5/OS TCP/IP FTP Server and click Continue.
6. Click OK on the Application Status screen.
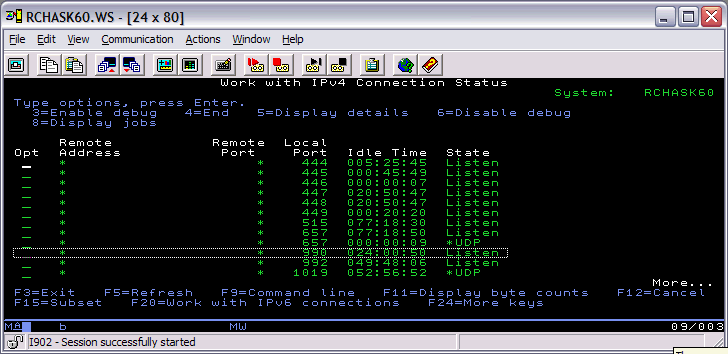
7. Restart the FTP server application ENDTCPSVR *FTP and then STRTCPSVR *FTP. Check NETSTAT option 3 to verify the FTP secure port is listening. You can use F13 to sort by local port and then F14 to display the local port to make it easier to find port 990 (the secure FTP listener).
Anyone who wants to connect to the FTP server securely will likely need the CA (Certificate Authority) of the certificate that was used to secure the FTP server. You can export this CA and send it to whomever requires it.
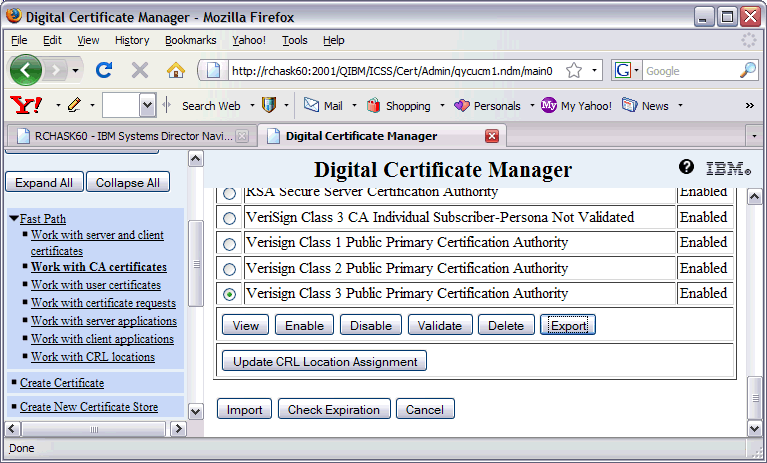
8. In DCM again, click on the Work with CA certificates option in Fast Path.
9. Select the CA certificate you wish to export. If it was a locally signed certificate, you will see LOCAL_CERTIFICATE_AUTHORITY. Select the appropriate radio button and click the Export button below.
10. Make sure the File radio button is selected and click Continue.
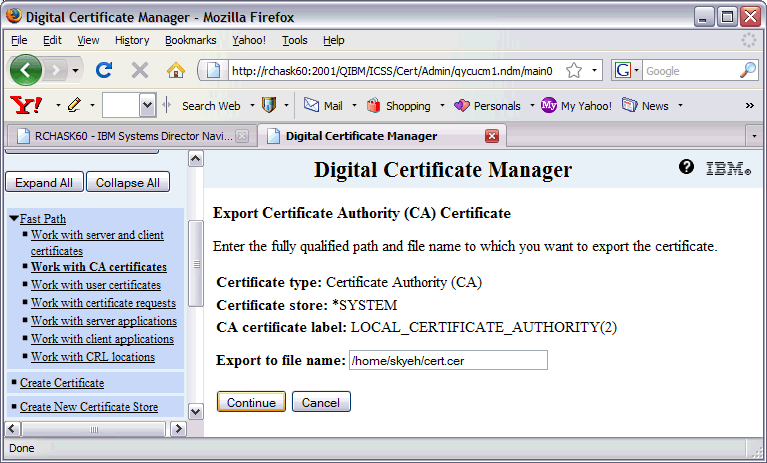
11. Fill in the Export to File name: field. This file will go to the IFS, and you must include the path and name of the file you are creating. For example, to export to your personal home directory in the IFS, you would specify /home/myprofilename/cert.cer where myprofilename is your directory and cert.cer is whatever you want to call the certificate file. The extension can be .txt, .cer, .crt, or just about whatever you choose. Note: Windows OS recognizes the .cer extension as a certificate and is probably a good choice to use.
12. Send the file to whomever requires it. You may need to move the file to your PC if you do not have software to send it directly from the i5.
The client will then import the CA to whatever application they use for client side FTP. They can then attempt to connect to the FTP server securely.
[{"Type":"MASTER","Line of Business":{"code":"LOB57","label":"Power"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"SWG60","label":"IBM i"},"ARM Category":[{"code":"a8m0z0000000CLbAAM","label":"Communications-\u003EFTP"},{"code":"a8m0z0000000CSxAAM","label":"Digital Certificate Manager-\u003EFAQs"}],"ARM Case Number":"","Platform":[{"code":"PF012","label":"IBM i"}],"Version":"7.1.0;7.2.0"}]
Historical Number
522844747
Was this topic helpful?
Document Information
Modified date:
04 August 2022
UID
nas8N1012980